Multi-Factor Authentication
Get secure, intelligent, and authenticated access with InstaSafe Multi-Factor Authentication (MFA) and Single Sign-On (SSO), ensuring your users' identities are verified. Achieve enhanced security with additional authentication layers such as OTP, T-OTP, PIN, biometrics, or push notifications.

Why does your Zero Trust Setup need adaptive Multi-Factor Authentication?
Avoid Identity and Credentials Theft
Protect accounts from identity theft with multi-factor authentication backing your Zero Trust Solutions
Enhanced User Experience
Single tap push notification approval. Simplified authentication and one tap login, straight from your mobile device, with InstaSafe Authenticator App
Reinforce your Zero Trust Setup
Extend adaptive Multi-Factor Authentication to all your users. Reinforce your Zero Trust model with secure single sign on to all applications
Adapt to the Hybrid Workplace
Seamlessly manage complex access requests for employees that work outside the office.
Protect Weak Employee Passwords
Put a lid on all weak passwords using multi-factor authentication that leverages passwordless authentication
Integrated security
Strengthen your Zero trust Secure Access stack with an additional layer of inbuilt Multi-Factor Authentication capability that supports your IAM infrastructure.
Types of MFA
InstaSafe provides additional factor authentication for web applications and email clients that support SAML or RADIUS authentication protocols. InstaSafe supports integrations with popular applications including O365, Zoho, Salesforce, Gitlab, Atlassian; and popular email clients including Zimbra, ICEWrap, Microsoft Office 365/ Exchange
Protocols Supported
SAML, OAuth, OpenID Connect.
Authentication Methods
OTP, T-OTP, MPIN, Biometrics, Push notification, Hardware Token
Compliance
PCI DSS, HIPAA, GDPR, SOX.
Authentication Methods Possibilities with InstaSafe MFA
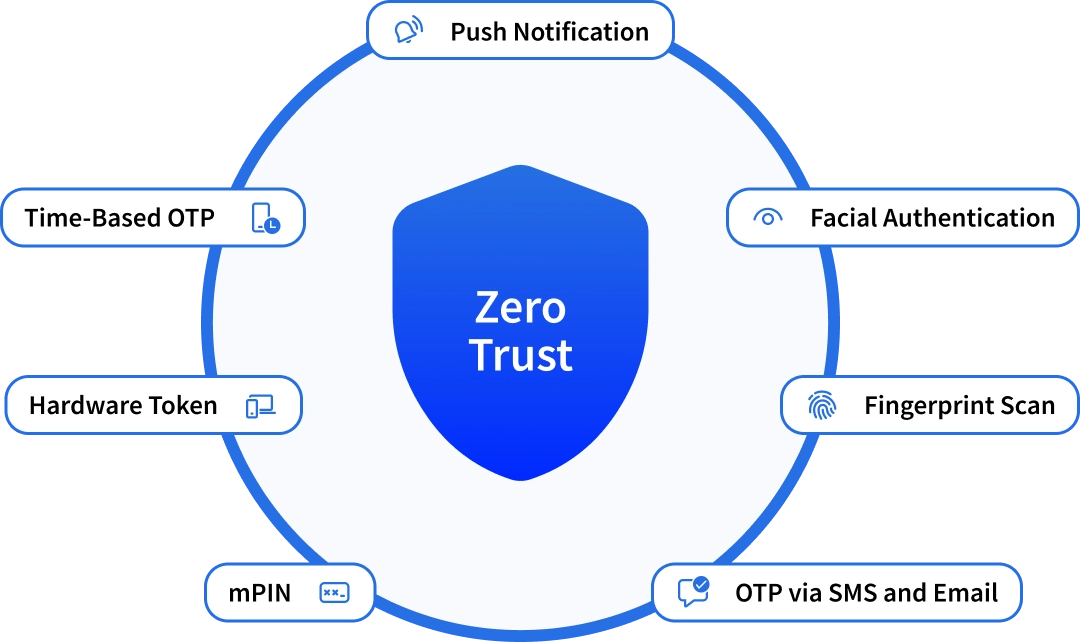
Some of the common Multi-factor authentication types are listed below:
Biometric Verification
The most used type of MFA is biometric verification, which includes fingerprint scan, retinal scan, voice recognition, etc. Users who have access to smartphones and laptops can implement this biometric authentication to strengthen their securityeasures. To implement biometric verification, users at the time of registration need to provide their fingerprint and facial scan. The system will store the information, and whenever the user accesses the device using face recognition or fingerprint, the access will be granted.
Phone Authentication (OTPs)
Another important MFA example is phone authentication using time-based OTPs sent to the registered number or email. It is generally a six-digit number code that is only valid for a limited period. To incorporate phone authentication, users need to provide the number and enable multi-factor authentication at the time of registration. So whenever a user accesses the account using credentials, an OTP will be sent. After entering the OTP, access will be granted.
Hardware Token Authentication
Another robust authentication type is the use of hardware tokens. These hardware tokens can be security keys or tokens which are in the user's possession. Whenever the user tries to access sensitive resources or data, applications or networks using credentials, a security key in their possession needs to be inserted into the device. This MFA authentication type is generally expensive compared to other methods and is usually employed by businesses that are ready to go the extra mile for security.
Software Token Authentication
Software token authentication is another type of MFA. In this authentication mechanism, mobile devices or authentication applications have been used to grant access. The organization needs to tie up with third-party authentication applications to grant access to their network. Since there is no need to carry any additional device like security keys, etc, this type of authentication mechanism is widely popular.
InstaSafe Authenticator capabilities include
Integrate with Any VPN
InstaSafe Authenticator can integrate with any VPN or remote gateway
Explore morearrow_forwardSupports major authentication protocols
It supports RADIUS, TACACS, OAUTH and SAML Authentication protocols
Explore morearrow_forwardPasswordless Authentication
Mobile app with various authentication methods available
Explore morearrow_forwardKey InstaSafe Authenticator Features
Continuous Facial Authentication
User can get authenticated to the application using their live face. Continuous facial authentication further checks the liveness of the user by monitoring the face every 30secs. If the user moves out from the frame of device screen or any third person comes infront of the device screen, the application gets automated logged out. This authentication mechanism is helpful for very sensitive business applications.
Read morearrow_forwardFIDO Authentication
FIDO (Fast Identity Online) is an Open and standardized authentication protocols developed by FIDO alliance aims to eliminate the password problem of authentication and Man in the middle attack associated with MFA hacking. FIDO authentication is based on public key crytography. FIDO allows users to sign in using passkeys. Passkeys are stored locally on the devices with the biometric information.
Read morearrow_forwardRADIUS Authentication
RADIUS is a client-server networking protocol that enables centralized authentication and authorization for a remote network. InstaSafe controller can act as a RADIUS server while prompting for MFA. Radius supports a variety of authentication methods, including PAP (Password Authentication Protocol), CHAP (Challenge Handshake Authentication Protocol), EAP (Extensible Authentication Protocol), and more.
Read morearrow_forwardTACACS Authentication
TACACS is a network security protocol that provides centralized authentication, authorization, and accounting services to access network devices and services. TACACS provide additional security feature compared to RADIUS as it uses a separate encryption key for each services. TACACS is associated with CISCO networking equipment and used to secure access to CISCO devices. InstaSafe controller can act as a TACACS server and enable authentication.
Read morearrow_forwardWindows Login
Windows Login is a simplified, secure authentication solution that improves the logon security of Windows Desktops, Servers, and Windows Terminal Servers, ensuring a secure login experience for your users. InstaSafe Authenticator can improve security posture by adding an additional factor of authentication when logging into Windows systems.
Read morearrow_forwardInstaSafe Authenticator Can Be Deployed in Both Public Cloud and On-Premises Data Center

Complement our Solution Stack
InstaSafe's MFA, powered by the Authenticator Application supports and complements InstaSafe's other Zero trust capabilities
Single Sign On
Validation and Authentication from a single dashboard, using a single set of credentials, gives you access to all authorised applications, whether on-premise or on the cloud
Explore morearrow_forwardSecure Remote Access
Leverage Multi-Factor Authentication along with InstaSafe ZTAA's least privilege segmented access capabilities to extend secure access to workforces across the world
Explore morearrow_forwardNetwork and Access Control Capabilities
Complement strong adaptive authentication policies with granular access policies to safeguard access to applications
Explore morearrow_forwardRisk Based Authentication
Leverage multiple factors of risk and trust assessment, including geolocation, temporal checks, device checks, and contact of request, before granting access
Explore morearrow_forwardBenefits of Multi-Factor Authentication
Eliminate Password Risks
Reduce password leaks arising from password reuse and weak passwords. With MFA, add additional layer of security from something you have or something you are.
Fast and Easy to Deploy
Implement strong authentication measures in a matter of minutes. MFA will seamlessly integrate with our existing Zero Trust Setup
Enhanced Security
Adaptive MFA is complemented by multiple other Zero Trust features like Behavioural biometrics, Geolocation,. Device Checks, Time Checks to streamline user access and predict user behaviour
Meets Regulatory Compliance
With MFA, highly regulated Industries such as banking, finance, insurance, and healthcare can adhere to better security controls for identity management.
Solve your access challenges with InstaSafe
Improve your security posture and gain better control over your network with Zero Trust
 CASE STUDY
CASE STUDYSecure Access to Office 365 Applications using InstaSafe Zero Trust
Continue Readingarrow_forward WEBINAR
WEBINAREnsuring a Secure Work From Home Environment: Remote Access Security Best Practices
Watch Nowarrow_forwardWhat Our Customers Say on G2
InstaSafe acts like a natural extension to our network infrastructure.
With its clientless functionality, it works seamlessly in the background, and causes no latency issues whatsoever during usage. The additional benefits of very quick scalability and adaptability to almost any environment make InstaSafe a lucrative option

Ranjith P
Chief Manager ISG& IS Audit
Good to use, easy to manage Zero Trust VPN security tool for cloud and ERP applications
InstaSafe has been instrumental in supporting the Information Management strategy of my organization by providing a secure foundation for our hybrid network infrastructure. We have managed to easily extend always-on connectivity and secure access to our cloud and ERP applications with Instasafe Zero Trust Access. It is much faster than a VPN and much easier to manage.

Hariharan S
Vice President
Demystifying IT Security
We have been able to deploy InstaSafe’s solutions seamlessly across a diverse workforce. The interface is user friendly, which reduces the need for extensive training, and the solution is flexible in many ways, allowing for better integration with our existing infrastructure

Rishu P
Business Development Manager
Reliable, easy to set-up, and scalable solutions
InstaSafe simply stands out in terms of its dynamicity and adaptability to expanding cloud environments. I would recommend InstaSafe for any company in the retail sector.

Vaibhav S
Assistant Consultant
Best VPN solution, very quick setup & a great support team!
InstaSafe simply stands out in terms of its dynamicity and adaptability to expanding cloud environments. I would recommend InstaSafe for any company in the retail sector.

Sadanand H
VP IT Infrastructure & Governance
Frequently Asked Questions on Multi-Factor Authentication
When it comes to MFA vs 2FA, 2FA requires only one additional security measure other than username and password. While MFA requires more than one security mechanism other than username and password. Based on the mechanism, MFA is considered more secure than two-factor authentication. Not just this, there are various two-factor authentication risks, such as phishing attacks, stolen devices, social engineering, etc.
The primary purpose of MFA is to add an extra layer of protection beyond just passwords, mitigating various threats. There are various risks of not having an MFA, such as credential theft, compliance concerns, insider threats, etc.
There are three main categories of authentication methods: something you know (e.g., password), something you have (e.g., security token), and something you are (e.g., biometric data).
Common MFA methods include using a password and security token, using a password and biometrics (e.g., fingerprint), using SMS codes, and using an authenticator app.
While no security method is completely foolproof, MFA significantly reduces the risk of hacking by requiring multiple layers of authentication. However, it is important to use strong and unique passwords, keep software and devices up-to-date, and be cautious of phishing attacks.
Multi factor authentication can be powered by various solutions and methods. The method can be password based or passwordless. Most prominent methods are mobile applications and the SMS,Email powered Time based One Time Password Authentication
MFA comes inbuilt at ZTA. the MFA can be enabled and configured for users at the Controller Admin portal. The controller will force the user for an MFA based on the user configurations.
Many times an external user wins over an authentication making use of various hacking methodologies such as bruteforce or Zero day exploits. Having an additional authentication will protect the applications and access by an additional layer of checks and security.
Zero Trust Application Access
Secure Single Click Unified Access to SSH/RDP Servers and Applications hosted anywhere, by workforces located anywhere
Zero Trust Network Access
Leverage granular access policies, passwordless authentication, and visibility across your network with the ZTNA solution
Secure Cloud Access
Empower your Remote Workforce to seamlessly connect and work securely, from Anywhere.
VoIP Access
Extend Secure Remote Communication Channels for Remote VoIP users with a Zero Trust Solution
Are you ready to be a part of the Zero Trust Secure Access Revolution?