InstaSafe Zero Trust Security Core Features
Review, approve, or reject any device. Only approved devices get to access applications.
Explore all features of the Zero Trust Platform
Instasafe Zero Trust Platform has a host of security features that make remote access experience seamless and secured. Learn why Instasafe Zero Trust is the best VPN alternative solution.
Device Authorization and Device Binding
Allows IT administrators to review and approve or reject new devices before they can access enterprise applications from the ZTAA agent. This will ensure that only trusted devices upon approval by the administrator, can access enterprise applications from the ZTAA agent.
Explore Morearrow_forwardDevice Posture Check
Empower IT administrators to ensure that only devices that comply with predefined security policies can access the enterprise applications from the agent. With more than 10+ parameters check capability, it greatly reduces the risk of device spoofing attacks.
Explore Morearrow_forwardAlways ON
With Always ON, VPN tunnel is established with the application as soon as user switches on their computer system. This creates better security for remote users rather than manually establishing connections.
Explore Morearrow_forwardDomain Joining
Empowers the IT teams to make the remote devices join the corporate domain, so they can then easily push policies using AD. Extend AD/LDAP compliance to all your remote devices and ensure compliance with our domain joining tool.
Explore Morearrow_forwardIdentity Provider for SSO
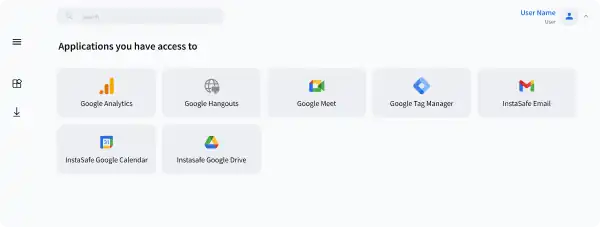
InstaSafe ZTAA can act as an single sign on solution for applications that support login via SAML
Explore Morearrow_forwardAgentless Access
With our agentless remote access, you can directly access any web- based application using a web browser access portal. No Client to install. Agnostic of any Operation System and any Browser
Explore Morearrow_forwardAre you ready to be a part of the Zero Trust Secure Access Revolution?