Zero Trust Access for the Modern Workforce
Secure access with the Zero Trust model for business-critical applications across multi-cloud environments, eliminating the pain of legacy tools
Unified Platform for Access, Authentication, and Control
Integrated suite of security solutions designed to provide robust protection for today’s distributed workforce.
Identity and Access Management (IAM)
Centralized control over user identities with role-based access, ensuring only the right users have access to the right resources.
Learn Morearrow_forwardZero Trust Network Access (ZTNA)
Secure access to applications based on identity, context, and device posture—eliminating implicit trust.
Learn Morearrow_forwardMulti-Factor Authentication (MFA)
Protect sensitive data by requiring multiple authentication factors before granting access.
Learn Morearrow_forwardSingle Sign-On (SSO)
Simplify the user experience with secure, one-click access to all enterprise applications using a single set of credentials.
Learn Morearrow_forwardContextual Access
Enforce dynamic access policies based on location, device, and user risk to prevent unauthorized access.
Learn Morearrow_forwardEndpoint Controls
Ensure that only compliant devices can access corporate resources by enforcing device-level controls.
Learn Morearrow_forwardHow InstaSafe makes the difference?
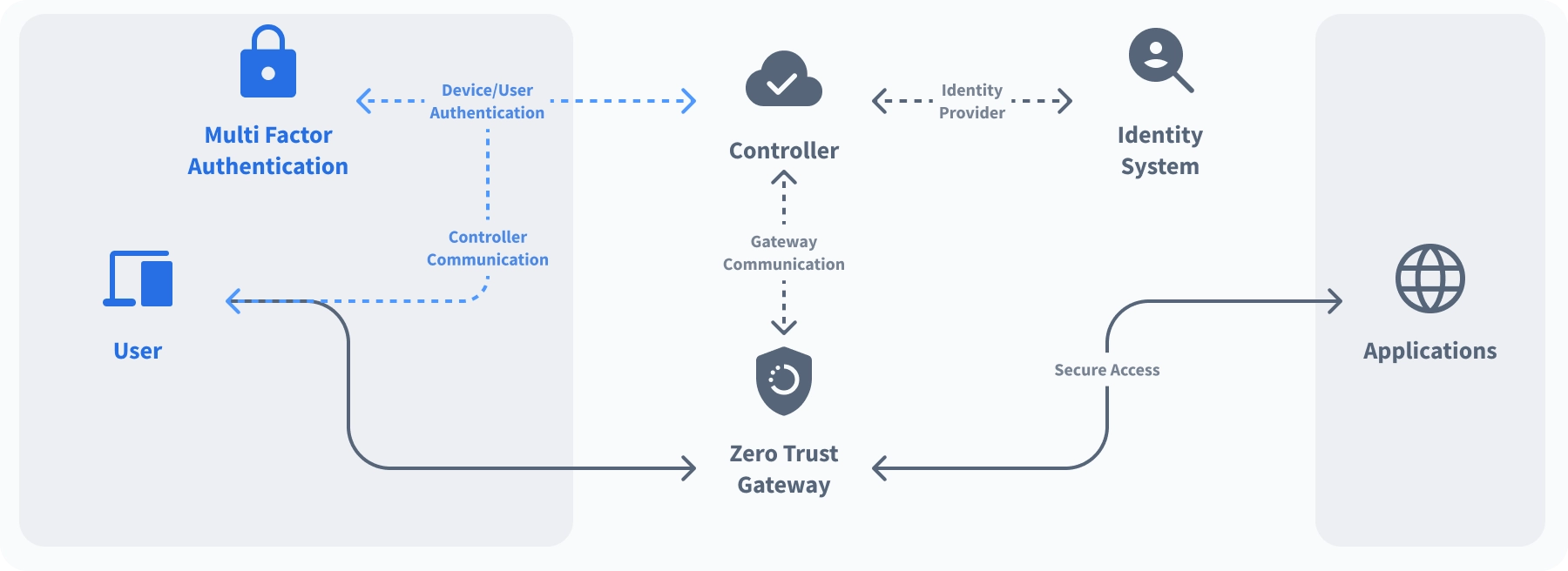
User identity and user device gets authenticated by the Controller using Multi factor authentication
Our Approach to Zero Trust
Moving Beyond the “Castle and Moat” Security Model to Zero Trust Security
Authentication Before Access
Combine seamless integration with IDP and AD, with integrated MFA and SSO capabilities to ensure secure and seamless one click access to applications
Know Morearrow_forwardGranular Access Controls
Set up access controls for applications, file and service access
Know Morearrow_forwardContinuous monitoring of Network & device behaviour
Get 360 degree visibility with easy integration with SIEM Tools
Know Morearrow_forwardThreat Intelligence and Alerts
Detect security events like invalid login attempts, bruteforce attacks; Check health of gateways and devices and provide alerts
Know Morearrow_forwardWhy InstaSafe Zero Trust?
Least Privilege Access
Leverage Granular Access Control and Role Based Access Policies to grant users the minimum access necessary to do their jobs
Know Morearrow_forwardBehavioural Authentication
Identify user impersonation attempts by analysing past user behaviours
Know Morearrow_forwardPrivacy First
Authenticate user and device identity without routing any customer data through vendor owned infrastructure, ensuring data privacy
Know Morearrow_forwardServer Blackening
Reduce your exploitable attack surface by making your assets completely invisible to the internet
Know Morearrow_forwardSegmented Application Access
Ensure that users can only access what they are allowed to access through application specific tunnels
Know Morearrow_forwardOne Click Secure Access
Combine seamless integration with IDP and AD, with integrated MFA and SSO capabilities to ensure secure and seamless one click access to applications
Know Morearrow_forwardDrop All Firewall
All data traffic coming to the IP is dropped, to avoid detecting presence of the IP address
Know Morearrow_forwardMulti-Device Support
Secure access to any on-premise or cloud based application, and grant secure access to any type of device.
Know Morearrow_forwardSeamless Support for your Stack
InstaSafe integrates seamlessly with every internal applications, databases, and cloud






What Our Customers Say on G2
InstaSafe acts like a natural extension to our network infrastructure.
With its clientless functionality, it works seamlessly in the background, and causes no latency issues whatsoever during usage. The additional benefits of very quick scalability and adaptability to almost any environment make InstaSafe a lucrative option

Ranjith P
Chief Manager ISG& IS Audit
Good to use, easy to manage Zero Trust VPN security tool for cloud and ERP applications
InstaSafe has been instrumental in supporting the Information Management strategy of my organization by providing a secure foundation for our hybrid network infrastructure. We have managed to easily extend always-on connectivity and secure access to our cloud and ERP applications with Instasafe Zero Trust Access. It is much faster than a VPN and much easier to manage.

Hariharan S
Vice President
Demystifying IT Security
We have been able to deploy InstaSafe’s solutions seamlessly across a diverse workforce. The interface is user friendly, which reduces the need for extensive training, and the solution is flexible in many ways, allowing for better integration with our existing infrastructure

Rishu P
Business Development Manager
Reliable, easy to set-up, and scalable solutions
InstaSafe simply stands out in terms of its dynamicity and adaptability to expanding cloud environments. I would recommend InstaSafe for any company in the retail sector.

Vaibhav S
Assistant Consultant
Best VPN solution, very quick setup & a great support team!
InstaSafe simply stands out in terms of its dynamicity and adaptability to expanding cloud environments. I would recommend InstaSafe for any company in the retail sector.

Sadanand H
VP IT Infrastructure & Governance
Solve your access challenges with InstaSafe
Improve your security posture and gain better control over your network with Zero Trust
 CASE STUDY
CASE STUDYSecure Access to Office 365 Applications using InstaSafe Zero Trust
Continue Readingarrow_forward WEBINAR
WEBINAREnsuring a Secure Work From Home Environment: Remote Access Security Best Practices
Watch Nowarrow_forwardAre you ready to be a part of the Zero Trust Secure Access Revolution?