Secure Access with Device Binding: A Core Feature of InstaSafe’s Zero Trust
Review, approve, or reject any device. Only approved devices get to access applications.

What is wrong with other free browsers?
Not for Enterprises
Free browsers are not built for enterprise users. There are not built keep security aspects in mind
Pop Up Ads and Redirects
Threat actors can force user redirect to malicious page with forced popup
Plugin Vulnerabilities
Vulnerable plugins can monitor user browser activity and can steal user credentials data
Weak Protection
Infected browser can steal password information and browser history data
Steps to Enable Device Binding Feature
Set Rules for Device Authorization
Rules that can be set based on company preferences
1. Allow First Device
2. New Devices will require Admin Approval
3. Allow First Device. Subsequent Devices will require Admin Approval
4. New Devices will be Automatically Approved after 'n' days

Device Approval by IT Admin
IT Admin can view the list of devices that are pending for approval. IT Admin can review it and further approve or reject.

Inventory Management and Monitoring
IT admin can view the list of approved devices in inventory and manage the devices.

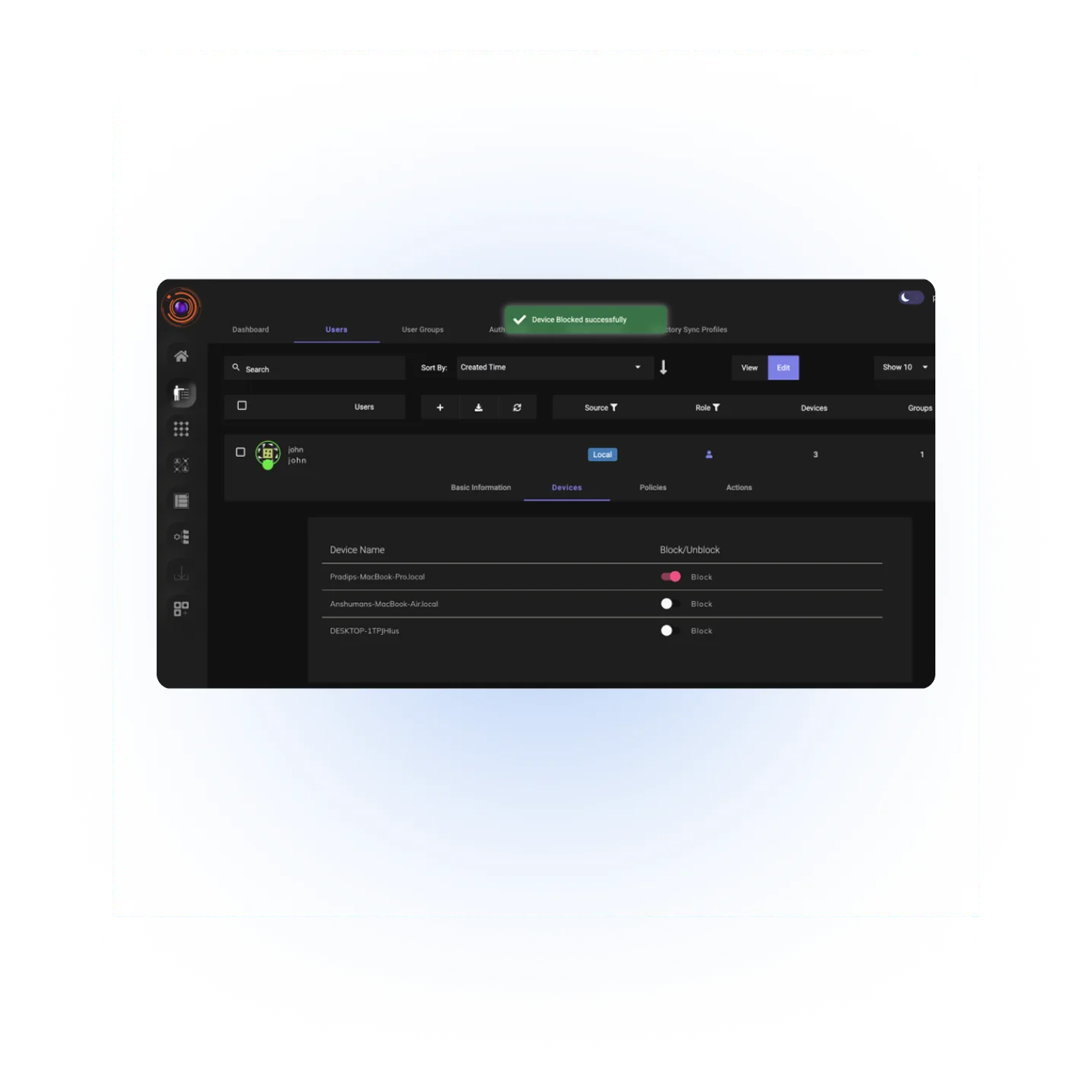
Blocking Approved Device
In case device needs to be blocked for any reasons, IT administrator can block from the device inventory
Benefits of Device Binding Functionality
Allow only Trusted Devices
Provide access to device that you trust. You can allow company owned device or specific device in case of BYOD.
Better Visibility
Get detailed information about device parameters such as device name, OS installed, device login location and several other parameters.
Better Device Management
Allow/ Block one or more devices from one particular user based on company rules.
Better Security Controls
Get notifications when a user tries to login from a different device other than registered and block access automatically.
Seamless Support for your Stack
InstaSafe integrates seamlessly with every internal applications, databases, and cloud






Frequently Asked Questions on Zero Trust Device Binding
Device Binding is a feature that allows IT administrators to review and approve or reject new devices before they can access enterprise applications or servers using the Zero Trust Access solution. This will ensure that only trusted devices upon approval are given access to enterprise resources.
Zero Trust framework suggests only user authentication is not helpful for secure access. Device authentication is another key additional layer to ensure secure access.
System MacAddress, System Serial number are some of the device parameters considered for device binding.
Device authorization happens when the user logs in from the device that matches with the registered device records and the device is pre- approved by the administrator for that particular user to access applications.
Device binding is also possible for Bring Your Own Device (BYOD) work policy. If the enterprise wants, it can create workflows to approve or deny devices based on the need.
Yes, users can be allowed to have multiple devices that can be binded and approved to use. Desktop and mobile devices are supported for device binding.
Zero Trust Application Access
Secure Single Click Unified Access to SSH/RDP Servers and Applications hosted anywhere, by workforces located anywhere
Zero Trust Network Access
Leverage granular access policies, passwordless authentication, and visibility across your network with the ZTNA solution
Secure Cloud Access
Empower your Remote Workforce to seamlessly connect and work securely, from Anywhere.
VoIP Access
Extend Secure Remote Communication Channels for Remote VoIP users with a Zero Trust Solution
Are you ready to be a part of the Zero Trust Secure Access Revolution?