Simplify your Zero Trust journey with InstaSafe
Find out why InstaSafe Zero Trust solution is the preferred secure access choice for enterprises of every size
Your security needs to evolve for the modern network
The issue with current VPN providers and technologies claiming to leverage Zero Trust is the simple fact that they not only expose IPs to external internet, but also fail to ensure that customer traffic remains private
Privacy Issues
VPNs allow data traffic to flow through and be inspected by their servers, which can be compromised and lead to exploitation of customer data
Exposed IPs
VPNs do not completely hide all enterprise assets from the internet, which can lead to exposed IPs being exploited by malicious users
Fragmented Access
The use of multiple access tools for accessing assets on premise and on different cloud environments creates a web of vulnerabilities
Zero Trust Solution Features
Simplifying Controls and Security of your Multi Cloud Environments with Cloud Access Security Solutions
Leverage SDP based principles and drop all firewall to ensure that visibility and the access to the applications and the infrastructure is limited to the authenticated users and authorised devices and the entire network is invisible to external users
Any shared customer assets are kept on a local network behind a gateway unseen by the external users
A drop all firewall at the gateway hides the presence of the gateway from the internet
Each application/server access by a user creates a secure individual tunnel controlling the user access within the tunnel
Only validated device/user combinations are given visibility to the network or the gateway
The authentication process involves user credential validation, MFA, and device posture validation

Customer Data belongs to the customer only. Your data traffic need not be inspected by your vendor machines. Any flow of your data through vendor machines exposes the risk of supply chain attacks. Ensure that data and authentication planes are separated and your data remains confidential and secure with InstaSafe
Separate Data Plane carrying critical data, from control plane where trust is established
Data Plane doesn't go through vendor machines, ensuring privacy for your data
Separation of planes protects against network based attacks
Your data is secured against supply chain attacks since enterprise data is inaccessible to vendor

Establish authorised encrypted application specific tunnels seamlessly and instantly with Single Message Authorization.
Any user trying to access enterprise apps must have visibility to the gateway
InstaSafe's controllers communicate any incoming access requests to the gateways through a special messaging mechanism called SMA
On validation of the message, the gateway allows port access, and a secure encrypted tunnel from user to apps is created
All of this happens seamlessly and instantly in the backend, without the involvement of the end user

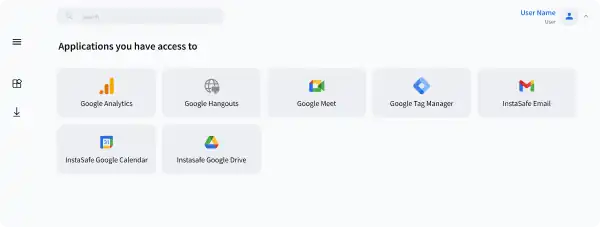
Simplify access to all data, servers and applications, hosted any where, with a unified access solution that can be managed from a single dashboard
Allow for seamless integrations with IDP and AD for easier identity management
Enable multifactor authentication capabilities along with SSO capabilities, with InstaSafe's own Authenticator applications
Ensure advanced monitoring and reporting capabilities through easy integration with SIEMs
Empower your security teams with Network Access and Control, IAM, and MFA capabilities from a single solution

Are you ready to be a part of the Zero Trust Secure Access Revolution?