Why should a Software Defined Perimeter replace your VPN?

With the outbreak of coronavirus, many organizations have opted for the work from home infrastructure. In this case, the IT teams are the ones that are under immense stress to ensure network security of all devices and data. However, this stress can be reduced using the latest technology to secure remote networks. This is why software-defined perimeter has made its way into the corporate sector. For the increase in zero-trust oriented needs of multinational companies, using VPN is not enough.
It is recommended to use SDP for a positive experience and enhanced security. Let us know more!
A software-defined perimeter known as SDP is a resource that is used to hide internet-connected infrastructure i.e. servers or routers. This is done so that it is not visible to the third parties or potential attackers, irrespective of the fact that it is hosted on-premises or in the cloud server. Here, the goal is to back up the network perimeter on software, rather than on hardware. Companies that use SDP are essentially covering their servers and other internet-connected infrastructure with a cloak of invisibility i.e. the SDP.
How does an SDP work?
A software-defined perimeter creates a virtual boundary surrounding the assets of the company at the base level i.e. the network layer. This boundary separates the network layer from other access-based controls that lead to restriction of user privileges, however allowing wide network access. An SDP also authenticates devices as well as user identity.
How do SDPs allow access to users?
SDPs allow access to the user only after the following steps:
- Complete verification of the identity of the user
- Accessing the state of the network or device
Clearly, the motivation for the software-defined perimeter is the added safety that the company can avail to.
After the authentication, the SDP sets up a separate network connection between the company asset and the new server that has been authenticated. Here, it must be noted that the new authenticated server is not given full access to a larger network. However, is granted its own network connection that is inaccessible to other servers that have not been approved by the SDP. Thus, making it a great source for VPN replacement.
How is SDP different from VPN?
While it has been seen that SDPs may consolidate VPNs into their infrastructure for strengthening the security of the network connections between the authorised networks and the devices, they are gaining immense popularity as an alternative to VPN. Therefore, SDPs are known as VPN replacement for Zero Trust Network Access and enhancing Remote Workforce Security, since many multinational companies have decided to allot work from home to their employees.
Why is it so? Let us find out!
SDPs are different from VPNs in the following ways:
- SDPs are more secure.
- SDPs do not share network connections.
- SDPs are infrastructure and location-agnostic.
- SDPs provide feasible features to protect on-premises or cloud infrastructure.
- Software-defined perimeter can be easily integrated with hybrid cloud or multi-cloud deployments.
- Capable to connect with users in any location, not just within the company’s physical network perimeter.
- Effective to manage Remote Workforce Security, especially during Covid-19.
- SDPs manage all users, endpoints and policies from a single console.
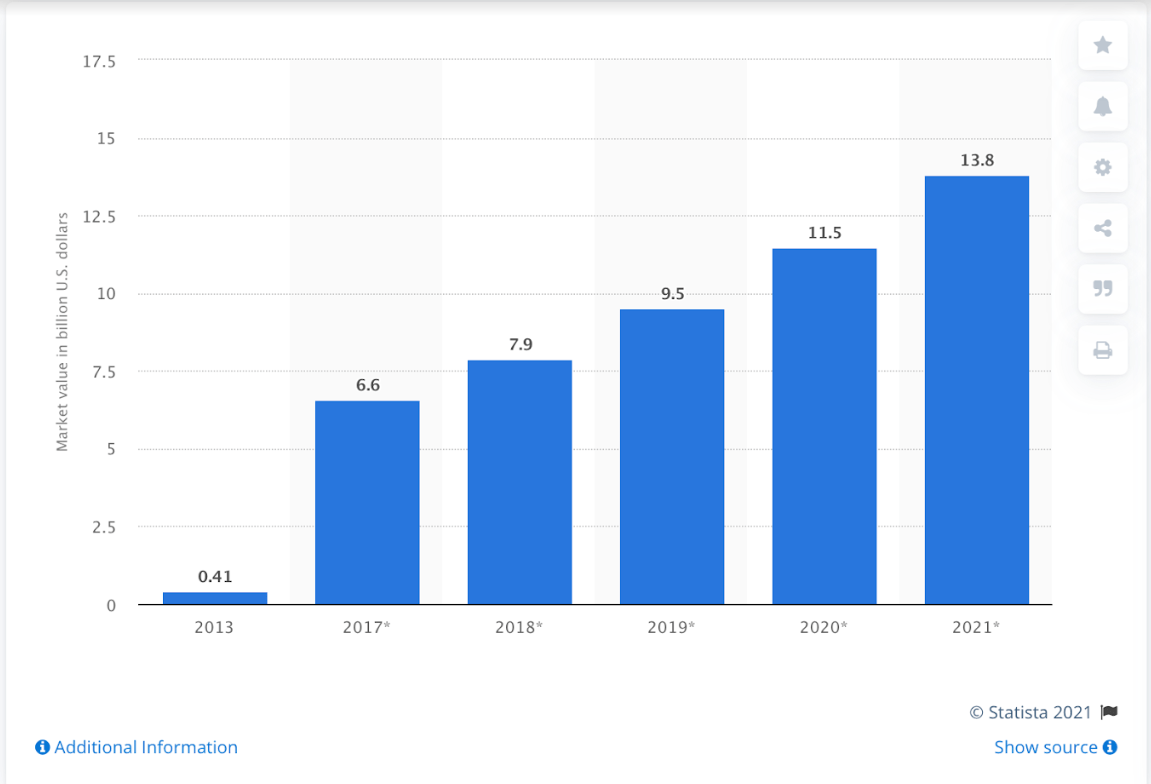
As per Statista, there is an increase in the size of the software-defined networking (SDN) market across the world, from the year 2013 to 2021. The expected reach was predicted to reach up to 6.6 billion U.S. dollars in size as per a study conducted in 2017. The below graph explains the study in detail.
Why SDP is a Perfect Alternative for VPNs
What to consider while considering SDP as a VPN alternative?
While we have shared many points for Motivation for Software Defined Perimeter, here are the factors you should take into account while replacing VPN with SDP:
- Performance requirements
Make sure that service-level agreements are available and uptime is scrutinized. Also, ensure the connectivity with the breadth in PoPs.
- Security requirements
It is vital to assess the network and its security capabilities to ensure if every provider has the same level of maturity.
What are the important features of SDP?
The motivation for Software-Defined Perimeter does not end here. Here are the major factors that companies keep in mind as they opt for SDP to avail of its latest features for the growth of their business— virtual and on-premises.
- Users can connect with both cloud services as well as on-premises resources using the SDP service. Every user, policy and endpoints are defined and applied via the SDP console.
- Software defined perimeter offers streamlined, optimised, and cloud-aware network access for various SaaS, IaaS, PaaS provider offerings.
- SDP combines various network threat detection capabilities into a common consolidator.
- Aggregates several network security and access control into a common secure network connection.
- The services integrate SD-WAN access and traffic optimization capabilities into common brokering services.
Well, Covid-19 has all multinational companies on their toes. Remote operations have made it difficult to ensure the security of the data shared from various devices from different geographical areas. However, this is where SDP comes into the picture and simplifies the management for the company, along with enhancing the security of the data.
If you are looking for professional help and a more influential Motivation for a Software-Defined Perimeter, InstaSafe is your go-to destination. The company’s Zero Trust solutions use Software Defined Perimeters to secure critical assets belonging to the organization. We are trusted by more than 100 companies across the globe as we believe in serving our customers as a priority, empowering organizations in their digital transformation journey, providing a user-friendly interface, seamless experience, maximum security and a secure connection.
If a secure remote connection is what all you are looking for, get in touch with us today!
Key Products
Zero Trust Application Access | Zero Trust Network Access | Multi Factor Authentication | IAM Identity And Access Management | Secure Enterprise Browser
Key Features
SSO Single Sign On | Endpoint Security | Contextual Based Access Controls | Always On VPN Connection |Clientless VPN | Device Binding | Device Posture Check | Domain Joining
Key Solutions
VPN Alternative Technology | Secure Remote Access Solutions | Cloud Application Security | DevOps Security | VoIP Security Solutions
