Choosing the Right Zero Trust Architecture
Zero Trust Network Access (ZTNA) is a next-generation accessible solution that is expected to replace long-standing Virtual Private Networks (VPN) as a significant component of IT managers' toolkits. When selecting the correct ZTNA architecture for your company, there are a number of factors and characteristics to consider.
This article will break down the distinctions between Software Defined Perimeter (SDP) and reverse-proxy designs, as well as how to assess them properly.
The Importance of a Zero Trust Architecture
VPN has been the dominant method of connecting professional staff to business applications for several years. So why are enterprises suddenly opting to migrate? Simply put, the VPN architecture is incapable of providing the level of security that is essentially necessary to safeguard against new cyber threats and trends. The utilization of VPNs in 68 percent of major incidents utilizing virtual private tools, according to IDC. Making risk reduction a primary motivating factor for many firms.
Identification of ZTNA as the technologies that will replace VPN with Gartner, Forrester, and many other analysts. Since it not only provides full security but also promises efficiency and work benefits to the organization. By 2023, 60% of businesses will have replaced most of their web connection virtual private networks (VPNs) with ZTNA. Gartner, Inc.
31% of enterprises consider ZTNA as reliable software, with 19% in the development phase.
- TeleGeography
Understanding the use cases that led to the adoption of Zero Trust Network Access (ZTNA) is critical for enterprises to develop their own evaluation criteria. ZTNA has a wide range of applications, including data access, restricted access, uncontrolled and BYO device support, and much more. You should consider the needs while selecting a ZTNA architecture for your organization and drive the uses.
Principles of Zero Trust Network Access
The main concepts of Zero Trust Network Access, which were first created by the Jericho Forum, can be described as five principles:
Not to Trust on Anyone
Before you grant access, all users and devices must demonstrate their trustworthiness. This is so important to businesses that Gartner estimates that 60% of them would abandon their remote access virtual private networks in favor of ZTNA by 2023.
Confirm identity claims
A fundamental of Zero Trust security is end-user identity and verification. It's so crucial, According to Centrify, 73 percent of companies have given their employees additional training on how to stay cyber-safe. While working remotely, with a focus on password verification and log-in credentials.
Give what you know to those who need it
Every user's rights start at zero and grant when absolutely necessary. In other words, it is least-privilege access because it allows users to connect to the tools they require while preventing them from accessing the ones that are not required. According to an IDC survey, 40 percent of cyber intrusions are caused by authorized users accessing illegal systems.
Device awareness
It is essential to guarantee that anonymous, susceptible, or infected devices do not gain access to corporate resources. According to IDC, 70 percent of successful intrusions start on the endpoint.
Play zone defense
Logically segregate each application and impose authentication and security checks prior to granting access to each. Discover and use these micro-tunnels that are necessary to avoid lateral motion which VMWare in roughly 60% of attacks.
Exploring the Zero Trust Architecture
For the sake of simplicity, we will consider the broad elevated architectures for both Software-Defined Perimeter (SDP) and reverse proxy. There are several subtypes for each design, and each execution is slightly different.
Software-Defined Perimeter (SDP)
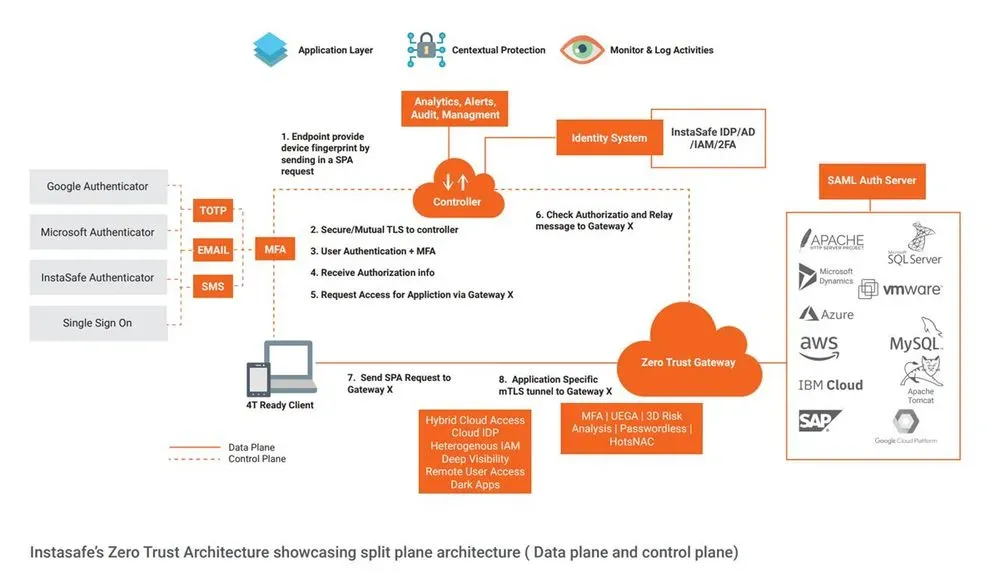
The Cloud Security Alliance's architecture is the foundation for the Software-Defined Perimeter, also known as Endpoint-Initiated ZTNA in Gartner's market guide. In this architecture, the software development is on approved end-user devices. It communicates with a ZTNA Controller about the device and its security environment. Data about the gadget, the user's identification, and other information can suggest whether to establish trust and include it in this centralized manner. The user will have the access to the software if all of the data and information satisfies the organization's policies.
High-level SDP architecture
Once authentication is complete, the ZTNA Administrator restricts access to any program; before that, the Gateway does not allow any traffic to pass. The application is essentially invisible because the Gateway rejects all traffic sent by unverified users and devices.
Using a reverse proxy
In the Gartner market guide, the reverse proxy architecture is similar to application-initiated ZTNA. Despite the similarity of the graphic, this architecture, which is the center of the BeyondCorp paradigm. It operates significantly differently than SDP, and there is no need for an endpoint agent.
Reverse-proxy architecture at a high level
This approach necessitates the installation of a connector, which generates outbound access to a ZTNA Proxy, on the same networking as the application. After that, users must verify with the ZTNA Proxy, which checks credentials against the company's identity management system. After authentication, authorization of traffic between the device and the application to flow through the proxy.
Evaluation of Various types of Zero Trust Architecture
Although there are some significant variations across the high-level designs, there should be no use of evaluation of individual solutions to eliminate suppliers without further investigation. Not all services are created equal, and development teams may have worked around the advantages and disadvantages of each alternative.
Although SDP Zero Trust providers have the option of using more advanced connectivity and security techniques they may have chosen to stick with more conventional protocols. Many developers employ common standards like IPsec or OpenVPN. They have a number of drawbacks, including latency and battery consumption on mobile devices. These provide minimal to no advantage over TLS-only reverse-proxy systems. It's crucial to choose vendors who use cutting-edge technology.
Application of Blockchain in Zero Trust Security
Blockchain technology can be used to increase the security of Zero Trust systems. By using a decentralized ledger, users can be authenticated without the need for a centralized authentication server. Additionally, the distributed nature of the blockchain makes it harder for attackers to compromise the system, as they would need to compromise all of the nodes in the network. Finally, blockchain-based systems can provide a secure audit trail that can be used to trace malicious activity back to its source.
Conclusion
The two most common models on which providers base their ZTNA technologies are software-defined perimeters and reverse-proxy architecture. They may appear to have little in common at first glance, but as this guide has demonstrated, there are differences in how they work and what they accomplish. Therefore, SDP solutions appear to offer improved security, networking flexibility, and system administration.
Key Products
Multi Factor Authentication | Identity And Access Management | ZTNA | Zero Trust Application Access | Secure Enterprise Browser
Key Features
Single Sign On | Endpoint Security | Device Binding | Domain Joining | Always On VPN | Contextual Access | Clientless Remote Access | Device Posture Check
Key Solutions
VPN Alternatives | DevOps Security | Cloud Application Security | Secure Remote Access | VoIP Security
