Solving the Excessive Trust Challenge in Remote Access Security

2020 alone accounted for 85% of the business enterprises using collaboration platforms (Microsoft 365, in this case) and SAAS productivity tools, falling prey to data breaches.
And, before you start reconsidering your digital transformation initiative and agendas, you must know that these breaches were related to a leak in email data!
When more and more of the work environments, ranging from mammoth enterprises to bean-sized start-ups are going remote, and have dispersed teams, you just cannot stop wondering – “What to share, and what not to?“
VPN slows down the entire performance and speed graph of an employee, and bypassing the same paves a way for security attacks and data breaches.
How? You may ask!
Then let us consider a simple example.
VPN Bypass or VPN Split Tunneling – How Employees Fall Prey to Becoming a Breach Beacon?
Simone works as a business analyst for an eCommerce enterprise and most of her time goes into collaborating with teams, clients and management. Being a business analyst, she has direct, non-questionable access to the entire organizational database. Also, she is using a number of BI tools, advanced analytics apps and collaboration platforms. However, using VPN kills the speed.
So, she uses her own mobile hotspot to ensure security, while steering away from the VPN. Now, one fine day, while she was sipping a coffee in her favourite cafe, she meets Ryan, her friend.
They plan to go to a musical this weekend and try to book the tickets. Her phone network is bad in the cafe and she uses the cafe WiFi. Without realizing it, she is now in the danger zone!
Her lines to the company database and enterprise resources are open for attack!
There are endless situations of this type where employees end up using their business laptops for accessing unsafe websites over unsafe or open networks.
Why VPN Fails Rising to the Occasion of Enterprise Security?
While there is nothing ailing the good old reliable security buddy – VPN, industry disruptions and modified work norms have certainly created new challenges.
1. Cloud-Based Apps
Cloud-based apps, such as Salesforce and Microsoft Office 365 and lots of others, have become a norm for enterprise productivity and collaboration. However, connecting back to the enterprise, just to access the internet and then use these apps begins to get in the way of the routine employee activity.
2. Confusion and Performance Hindrance
VPN-based cloud app access enforces remembering which apps require VPN and which don’t. This creates confusion and also becomes a performance hindrance for the employees.
Further, VPN slows down the cloud apps notoriously – the more an app is interactive, the more it is slowed down – and employees get frustrated over time.
From helpdesk support to cloud-based alternatives to interval security measures, like VPN – they look for anything and everything that can help them get things done fast!
3. Bypassing VPN Creates New Security Concerns
It is extremely common for your employees to go to great lengths, just to avoid VPN, exposing your internal network, assets and data!
It is during this time, that their devices are compromised, get bot infested, and become a beacon for security attacks later.
When these employees use the enterprise VPN, they have unlimited access to any database, any server, and any other confidential business asset.
So, how to solve this?
Let us find out!
Solving Trust-Based Security Challenges
Solutions for trust-based security challenges have two roots – controlling user access and establishing perimeter security.
And, both of them have their foundations in the “explicit trust” approach.
Let us start with the “explicit trust” approach.
Take a look at the following visual showing how implicit and explicit trust look like:
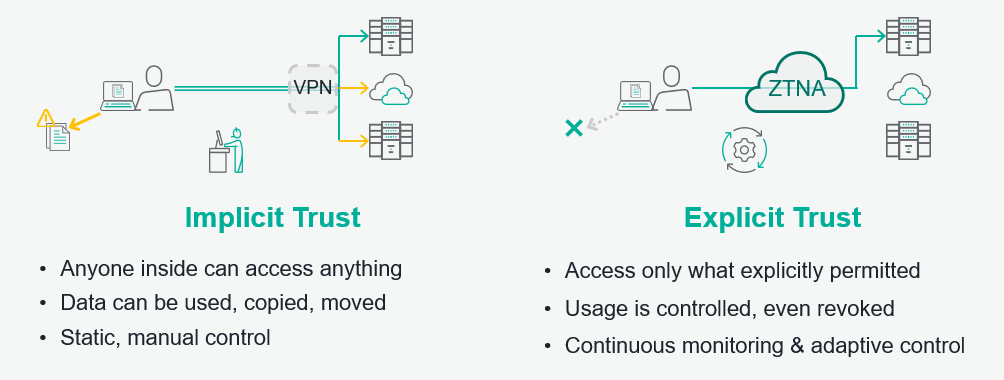
Source
Explicit Trust – What, and Why?
The traditional enterprise security approach relies on implicit trust where all the internal connections or network entities coming via VPN are given a carte blanche. Be it apps, information, company resources and data – there is no check post to authenticate and validate these entities.
Examples include employees logging in to the company server using their credentials and accessing the FTP server without any further authentication.
This will allow the bot-infested devices to become beacons for security attacks and data breaches.
On the other hand, the explicit trust approach has explicit access, modification, and update rules. The access and usage are monitored, controlled, and can be revoked as well, in the light of uncommon behaviour. This approach also exercises adaptive control.
For example, even when an employee is logged in, he has to pass through various validation and authentication checks to access, move, update or download the data or information.
Now, let us discuss the two pillars of trust-based security.
1. User Access and Activity Management
User access and activity monitoring are crucial for ensuring enterprise security at all times. Also referred to as UAM or User Activity Monitoring, it tracks user’s behaviour in the enterprise and over its networks.
Understanding the way users interact with the enterprise resources and data allows you to counter:
- Insider threats
- Human errors
- Malicious intent
Stemming from the Zero Trust Policy, UAM adheres to the – Never Trust, Always Verify – approach.
2. Perimeter Security
Perimeter security means having a Zero Trust network access approach, where every access to the enterprise network is tailored to just the specific apps and assets it might require. You can think of it as having private surveillance and a security monitoring system for your home located in a highly secure gated community with common surveillance.
For example, if a support employee is accessing a database not relevant to him, the access will be blocked. If he needs that information, specific data blocks will be made available for a specific time only via higher management.
This approach has two benefits:
- The networking teams can keep on providing remote access to the line-of-business apps.
- The security teams retain complete visibility and control required to keep the enterprise data safe and secure.
Take a look at the following visual that shows how a Zero Trust perimeter security keeps an enterprise safe.
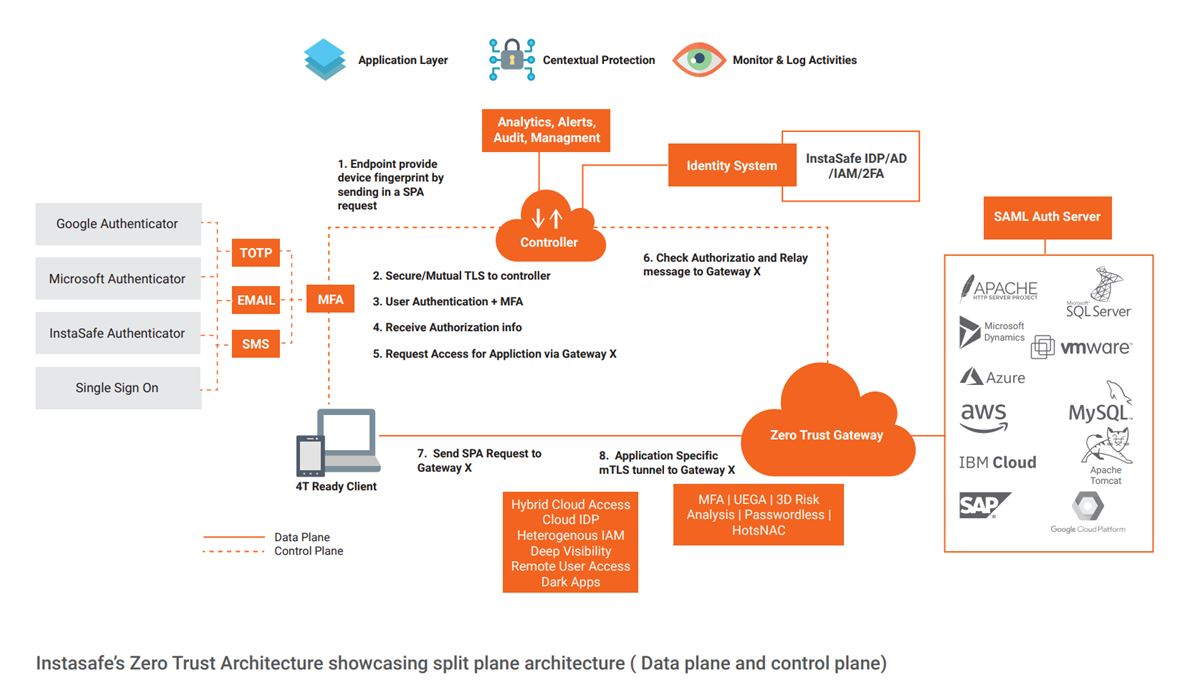
Solving Trust Challenges: Choosing the Right Partner
While the solutions discussed above are highly secure and are being used widely, they increase the access management and usage monitoring overhead for the security department.
The solution is, to invest in a highly streamlined, secure and robust Zero Trust Security Solution provider that can help you do all this without much ado, such as Instasafe.
The InstaSafe Perimeter Network Security with Zero Trust Policy is built to deliver performance and speed all the while keeping your perimeter security intact.
For more information, book a demo today!
Key Products
Zero Trust Application Access | Zero Trust Network Access | Multi Factor Authentication | IAM Identity And Access Management | Secure Enterprise Browser
Key Features
SSO Single Sign On | Endpoint Security | Contextual Based Access Controls | Always On VPN Connection |Clientless VPN | Device Binding | Device Posture Check | Domain Joining
Key Solutions
VPN Alternative Technology | Secure Remote Access Solutions | Cloud Application Security | DevOps Security | VoIP Security Solutions
