What Is Public Key Infrastructure (PKI) and How Does It Work?
Cybersecurity has numerous branches and encryption is one of them. Encryption is a way to encode the data and information to save it from unauthorised access.
Since concerns regarding cyber threats and confidentiality have triggered various technological advancements, we have seen different variations in a number of authentication solutions.
PKI authentication is a huge segment in the field of cyber security under the label of encryptions. Let’s understand more about the same!
What is PKI Authentication?
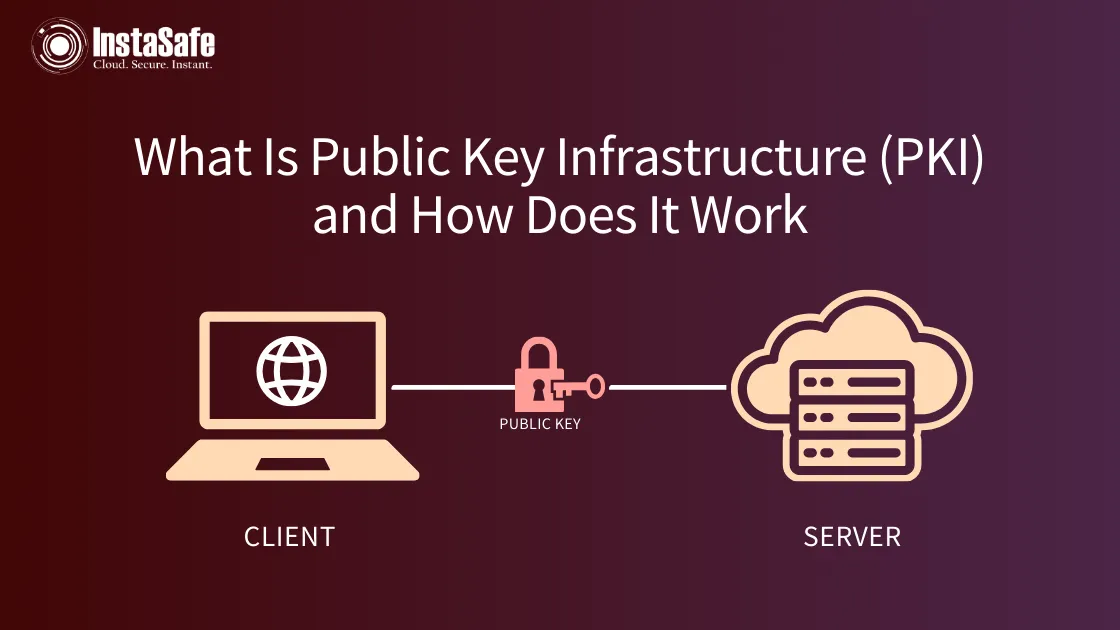
PKI in cyber security stands for Public Key Infrastructure and is a type of authentication used by various networks when needed. When passwords started feeling a little risky, encryption codes were invented. PKI is a result of this invention!
PKI authentication, through a cybersecurity solution of encryption certification, protects and enables safe communication between servers and clients, i.e., your website and your clients. PKI encryption assists trusted authentication and identification of the user and allows the rightful user access to the network or information.
This is possible with the help of (most commonly) a public key (a passcode that everyone knows) and a private key (a passcode that only the concerned user knows).
It provides optimal security and maximises the trust between your network and users. Since a lot of sensitive communication is carried out on the website, it is necessary to make the clients and customers feel safe and comfortable within your network. PKI in network security is a step towards this safe environment!
So, what is the PKI certificate of authentication used for, and how is it used? Let’s understand!
Components of PKI Authentication
1. Digital Certificates
A digital certificate is a certificate that authenticates the communication between the main server and a particular user or device. This is issued to the user by the server and its agents as an authorised identification tool.
This enables digital communication between servers and clients. It is also called a public key certificate.
2. Certification Authority
The digital certificate mentioned above is issued to the users by the Certificate Authority (CA). This authority is capable of accepting or denying these certificates to individuals or computer systems.
This digital agent issues the certificate to credible and trusted users, stores them in the network’s system and signs these certificates to authorise their use. The private and public keys are assigned to the users by this CA.
3. Registration Authority
The Registration Authority (RA) authorises the Certification Authority to sign, store, issue, and provide digital certificates to these individual users.
The basic function of an RA is to verify the identity of the user or system and authorise their certificate through registration.
4. Certification Management System
When the certificates are requested, received, revoked, or re-assigned to various users, the information is stored and managed by a digital agent and is called a certification management system (CMS).
5. Other Important Components
There is something called a certificate database. It is a database that stores the data regarding user certificates in a virtual format.
The certificates, data related to these certificates, their active period, etc., are stored on this database. The central directory is a location, a virtual secure location that stores passkeys.
How Does PKI Authentication Work?
There are two types of encryption PKI uses, and they are:
Symmetrical Encryption
- Symmetrical encryption is a straightforward and simplified use of the authentication process using passcodes to encrypt and decrypt the data.
- When we talk about symmetric encryption, you must understand that it comes with only one passcode and that is the private key.
- When the user types a message, it gets encrypted into something else.
- To decrypt this message, one has to enter the private key and then read the message.
Asymmetrical Encryption
- Asymmetrical encryption, however, isn’t straightforward to understand or perform. It consists of two passcodes, the private and the public key.
- The simplified cryptographic algorithm used to create the public key used in symmetric encryption is used to create a private key as well.
- So, when the user enters the message, it gets encrypted, just like symmetrical encryption.
- However, to decrypt or to read the message that has been encrypted in mathematical permutations, you will have to enter a passcode, and it is not publicly known.
- It is a private key, only known to the server or the individual behind that. One has to enter this private key in order to decrypt and read the message sent by the user.
So, why are digital certificates important for PKI authentication when the passcodes get the work done?
As mentioned above, digital certificates, like SSL certificates, act as security passes. They make the website or network more trustworthy, visible and better. Not only that, they also verify and authenticate the ownership of public and private passkeys.
These certificates also verify that the passcodes, public and private keys, are with the rightful owners only and not with an unauthorised party. This ensures smooth and secure communication between the user and the server, making sure there is no third party involved or reading the messages.
Conclusion
PKI authentication, specifically symmetric encryption, was even used in World War II to send secret messages so that the enemies wouldn’t be able to intercept or eavesdrop on transmitted messages. The modified, upgraded, and better version of that technology is what we call the PKI authentication nowadays.
It is important to maintain confidentiality when it comes to client communications. Hence, purchasing services that can protect your network has become a necessity, be it the Public Key Infrastructure or Multi-Factor Authentication solutions.
What is even more important is to buy these security solutions from trusted brands and providers like InstaSafe. This ensures sustained security and greatly cuts down on data breaches and unauthorised access to your networks.
Frequently Asked Questions (FAQs)
1. Is SSL the same as PKI?
SSL, the secure socket layer, is a technology that securely verifies and identifies the credibility of a website. However, it is not the same as PKI. It is a security protocol that uses PKI authentication for its benefits.
2. Where is PKI famously used?
PKI is used for email authentication, signing documents, securing web communications, encrypting files, decrypting files, securing local networks, etc.
3. Is PKI an application?
PKI is a set of hardware, protocols, processes, software, and procedures used to create, manage, distribute and invoke/revoke digital certificates. It is more of an infrastructure used to meet different security requirements.
Key Products
Multi Factor Authentication | Identity And Access Management | ZTNA | Zero Trust Application Access | Secure Enterprise Browser
Key Features
Single Sign On | Endpoint Security | Device Binding | Domain Joining | Always On VPN | Contextual Access | Clientless Remote Access | Device Posture Check
Key Solutions
VPN Alternatives | DevOps Security | Cloud Application Security | Secure Remote Access | VoIP Security
