What is a Software Defined Perimeter? How Does it Work?

Evolution of the term ‘perimeter’
The military definition of the term ‘perimeter’ is simple - we are inside and the enemy is outside.
Corporate networks had initially been designed to keep external threats outside, and internal assets secured from these threats. The internal network was deemed trusted by default, and everything outside was considered untrusted by default. Any resource trying to gain access from outside had to undergo scrutinisation from multiple security technologies.
This is still the foundation for most networking professionals even though a lot has changed since the inception of the design. In cyber security, the term is tuning to something different over the last two decades. In the early 2000’s the concept of firewalls and virtual private network (VPN) emerged widely for corporations to establish connectivity that are network centric approaches. Organizations establish SSL VPN and Wifi networks that enable people, such as partners to access the corporate network.
During 2007, Jericho forum published commandments, a list of 11 principles that define what must be observed when planning for security in the new world. According to the Jericho Forum, the Deperimeterization “has happened, is happening, and is inevitable” and organizations should “plan for it and should have a roadmap of how to get there. Historically, enterprises deployed perimeter security solutions in the datacenter to protect their critical applications from external threats. Later in 2013, Cloud security alliance (CSA) published a paper on Software defined perimeter based on it's working group to demystify this term for modern secure business use-cases.
Emergence of the Software Defined Perimeter
With adoption of BYOD (bring your own device), having contractors and partners within corporate networks, over permissions for users to have access to systems, Cloud concepts such as IaaS, PaaS and SaaS made the term ‘perimeter’ irrelevant due to security consequences, as they are based on hardware technologies. Software defined perimeters (SDP) replaces physical appliances with logical components that bring together standard security controls such as PKI, TLS, IPSec, SAML and concepts such as federation, device attestation and geo-location to enable connectivity from any clients to any information resource. Software defined perimeter solution mitigates most common network based security attacks by dynamically creating one-to-one network connections between users and the data they access.
Software defined perimeter (SDP) Architecture
Typical SDP architecture made up of three components namely SDP client, SDP controller and SDP gateway as shown in the reference architecture. The SDP client runs on each device, the SDP controller authenticates with identity provider and enforces policy based on the configuration granting users to access data, the SDP gateway acts as broker to protect resources.
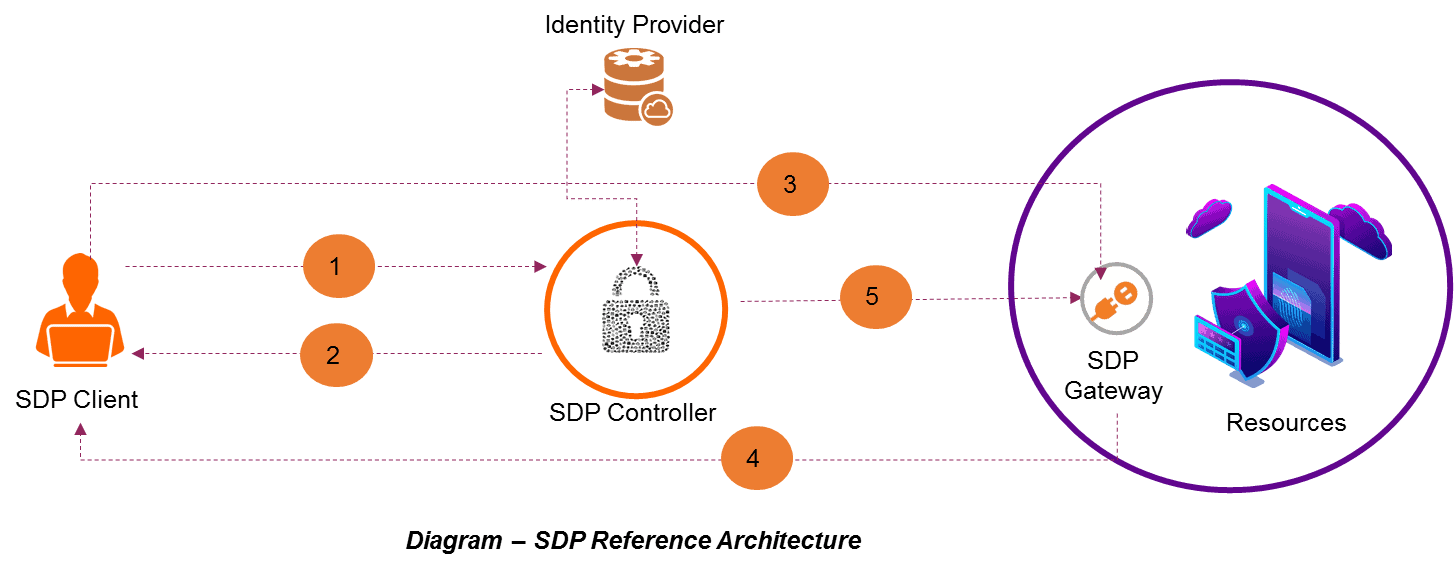
The Software-Defined Perimeter Solution (SDP) Works are as follows:
- SDP client device authorization requests will be validated by SDP controller and it applies the access policies that is based on combination of attributes such as user profiles, device status, location and infrastructure fingerprint.
- SDP controller returns a cryptographically signed tokens to the SDP client after checks the context, that authorize to access set of resources
- SDP client uploads live entitlements that SDP gateway uses to discover resources or applications matching the user's context.
- SDP gateway and SDP client establish a mutual session dynamically allocated to access the resources, if granted via encrypted tunnel. Access logs are recorded for audit purpose
- SDP controller continuously monitors for any context changes and ensures session segmentation between the SDP client and resources.
Software defined perimeters (SDP) security use-cases
Organizations today adopt security strategies based on numerous factors, that includes the ‘software defined perimeter’ solution part of their overall cyber security program. The key security use-cases are
- Work from home - enterprise workforce today require access to corporate resources from their home. With user credentials being compromised and arise in insider threat, organization need to ensure protection of critical data based on ‘need to know’ basis
- Adherence to compliance - SDP avoids additional costs associated with audits, as it provides visibility and control on systems on networks outside of the protected network.
- Utilize existing investments - Ability to augment capabilities with existing network security solutions potentially doesn’t enforce to ‘replace’ all of the investments. SDP solution shall integrate with most of the enterprise networking and security APIs
- Cloud workload migration - SDP provides a controlled path to move applications from datacenter to cloud.
Identity centric security - user based security protection strategies replaces the pitfalls exists in network / IP source based access control mechanisms.
Key Products
Multi Factor Authentication | Identity And Access Management | ZTNA | Zero Trust Application Access | Secure Enterprise Browser
Key Features
Single Sign On | Endpoint Security | Device Binding | Domain Joining | Always On VPN | Contextual Access | Clientless Remote Access | Device Posture Check
Key Solutions
VPN Alternatives | DevOps Security | Cloud Application Security | Secure Remote Access | VoIP Security
