What Is a Reverse Proxy?
In the vast and complex world of Internet networking, a reverse proxy serves as a crucial intermediary that plays a pivotal role in protecting, optimising and managing web server interactions.
Unlike traditional networking solutions that might seem abstract or complicated, a reverse proxy is essentially a smart traffic director who sits in front of web servers, carefully managing how client requests are processed and responded to.
Understanding Proxy and Reverse Proxy Fundamentals
Before delving into the specifics of reverse proxies, it's essential to understand the concept of proxy servers. A proxy is fundamentally a networking intermediary that acts on behalf of other devices, bridging communication between different network entities.
Think of it as a sophisticated messenger that carries requests and responses between clients and servers, adding layers of functionality and protection.
Traditional proxy servers come in two primary variations: forward proxies and reverse proxies. A forward proxy typically operates from the client's perspective, sitting in front of client machines and intercepting their outgoing requests.
When a computer sends a request through a forward proxy, the proxy forwards that request on its behalf, effectively masking the client's original identity and providing additional services like content filtering or anonymity.
What is a Reverse Proxy?
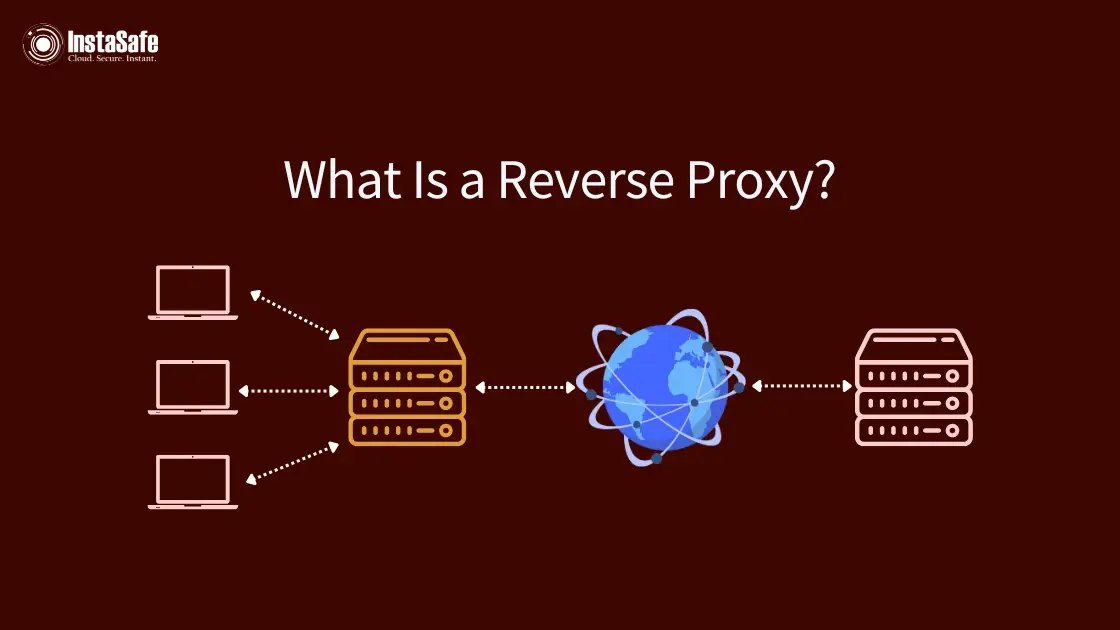
A reverse proxy functions from the viewpoint of the server. Instead of being in front of clients, a reverse proxy server is placed in front of one or more web servers. Requests made by clients to a website are first received by the reverse proxy, which then routes them to the relevant web server and sends the client the server's answer.
The key distinction is subtle but significant: while a forward proxy protects clients, a reverse proxy protects servers. When a client connects to a website with a reverse proxy in place, they interact with the proxy server, which appears to be the origin server. The actual web servers remain hidden behind this protective intermediary.
How Does a Reverse Proxy Work?
Let's break down the typical workflow of a reverse proxy:
- A client sends a request
- The request first reaches the reverse proxy server
- The reverse proxy evaluates the request and determines which backend web server should handle it
- The request is forwarded to the selected web server
- The request is sent to the server, which sends an answer back to the reverse proxy
- The reverse proxy receives the response and forwards it to the original client
Throughout this process, the client remains unaware that their request was intercepted and managed by an intermediary server.
Key Benefits of Using a Reverse Proxy
Enhanced Security
One of the most critical advantages of a reverse proxy is its ability to shield web servers from direct external access. By hiding the IP addresses and configurations of backend servers, reverse proxies make it significantly more challenging for potential attackers to target the actual infrastructure.
This approach provides a robust first line of defence against various cyber threats, including distributed denial-of-service (DDoS) attacks.
Load Balancing
Websites and applications experiencing high traffic volumes can struggle with performance when relying on a single server. A reverse proxy can distribute incoming client requests across multiple backend servers, ensuring no single server becomes overwhelmed.
This load-balancing mechanism helps maintain optimal performance, reduces response times and increases the overall reliability of web services.
Caching and Performance Optimisation
Reverse proxies can cache content from origin servers, dramatically improving website performance. When someone requests content, the reverse proxy can serve cached versions directly, reducing the load on backend servers and decreasing response times.
For instance, if a user in Paris requests content from a server located in Los Angeles, a local reverse proxy can cache and serve that content much faster.
SSL Encryption Management
Handling SSL (Secure Sockets Layer) encryption can be computationally expensive for origin servers. A reverse proxy can be configured to manage SSL decryption and encryption, offloading this resource-intensive task from the backend servers. This allows web servers to focus on their primary functions while the reverse proxy handles secure communication.
Global Server Load Balancing
Advanced reverse proxies can route client requests to servers geographically closest to them. This global server load balancing reduces latency by minimising the physical distance data must travel, resulting in faster and more responsive web experiences.
Implementing a Reverse Proxy
Organisations looking to implement reverse proxy technologies have multiple strategic options available. While custom development remains a possibility, it demands significant technical resources and substantial financial investment.
Many businesses find more practical approaches through third-party solutions that offer robust functionality with minimal internal complexity.
Content Delivery Network (CDN) services have emerged as particularly attractive alternatives, providing comprehensive reverse proxy capabilities without requiring extensive in-house engineering. These services offer scalable, managed solutions that can handle complex network traffic management with minimal organisational overhead.
Open-source platforms like Nginx, Apache and HAProxy have also become popular implementation choices. These platforms provide flexible, customisable features that can be tailored to specific organisational requirements.
They offer extensive configuration options and benefit from community-driven development, allowing organisations to adapt the technology to their unique network architectures.
Successful reverse proxy implementation requires a strategic approach. Organisations must carefully analyse their network infrastructure, assess security requirements and develop comprehensive performance benchmarking strategies.
The deployment process involves understanding specific traffic management needs, evaluating long-term scalability and ensuring the solution aligns with existing technological ecosystems.
Challenges and Considerations
Implementing reverse proxy technologies is not without significant challenges. Technical complexity stands as a primary concern, with frequent application updates requiring continuous proxy reconfiguration and complex version compatibility management. Organisations often encounter risks of service interruptions during implementation and integration processes.
The protective scope of reverse proxies presents another critical consideration. These technologies primarily safeguard sanctioned resources, which means unsanctioned or legacy applications may fall outside their protective domain. This limitation can create potential vulnerabilities in comprehensive network security strategies.
Performance implications represent another crucial factor. Introducing an additional network layer inevitably introduces processing overhead and potential latency in request-response cycles. Organisations must invest in continuous performance tuning and optimisation to maintain efficient network operations.
Security remains a persistent challenge, with the constantly evolving threat landscape demanding ongoing vigilance. Maintaining robust security configurations, ensuring regulatory compliance and addressing emerging cybersecurity challenges require continuous attention and strategic adaptation.
Ultimately, successful reverse proxy implementation demands a holistic approach. Organisations must conduct comprehensive infrastructure assessments, develop robust monitoring mechanisms and maintain technological flexibility. The key is to plan strategically, pilot testing and be dedicated to always learning and improving.
Conclusion
A reverse proxy is far more than a simple networking tool — it's a sophisticated solution that enhances web infrastructure security, performance and reliability. By acting as an intelligent intermediary between clients and servers, reverse proxies help organisations create more robust, scalable and secure web environments.
Protect your digital fortress with Instasafe Multi-Factor Authentication. We shield your critical systems from unauthorised access and transform your cybersecurity by adding intelligent, adaptive layers of verification beyond traditional password protection.
Key Products
MFA | I&AM | ZTNA | Zero Trust Application Access | Secure Enterprise Browser
Key Features
Single Sign On | Endpoint Security | Device Binding | Domain Joining | Always On VPN | Contextual Based Access | Clientless Remote Access | Device Posture Check
Key Solutions
VPN Alternatives | DevOps Security | Cloud Application Security | Secure Remote Access | VoIP Security
