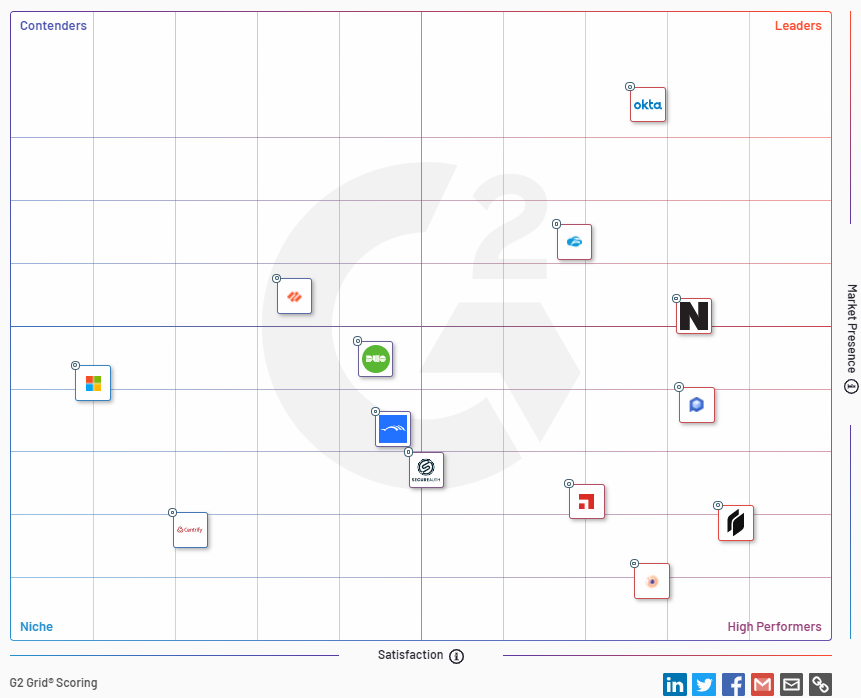
Instasafe has featured as 'High Performers' on G2 Grid for Zero Trust Networking software Category
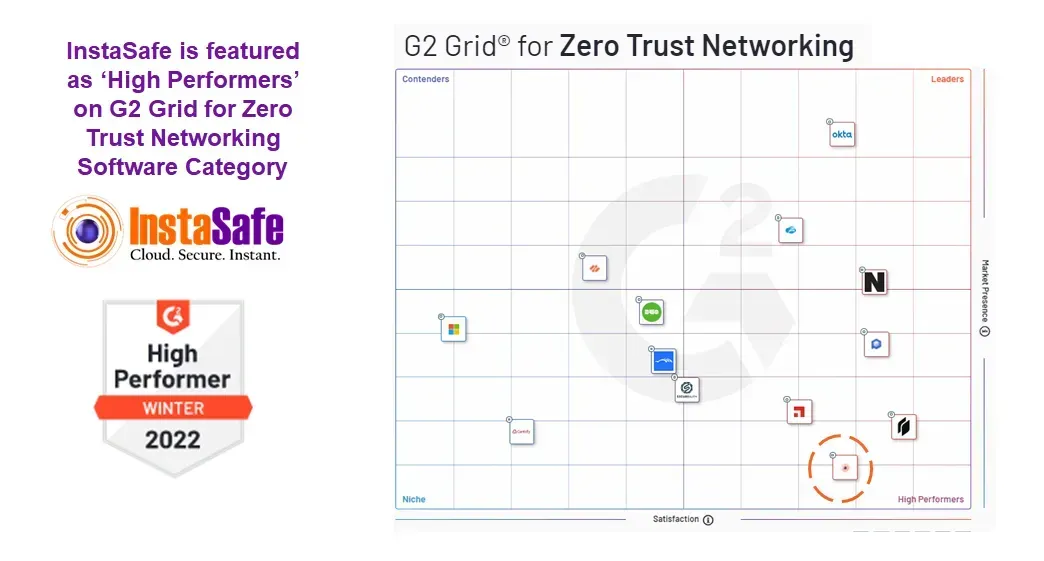
G2, a leading peer to peer review site published its Winter 2022 report on Zero Trust Networking Software. We are happy to announce that InstaSafe is featured on the "High Performers" Category along with other leading software vendors. High Performing products have high customer Satisfaction scores. We are thankful to all our customers and partners for believing in our product.
Check our what our customers say about Instasafe Zero Trust product in this link https://www.g2.com/products/instasafe-technologies-pvt-ltd-instasafe-ztaa/reviews
G2 Grid for Zero Trust Networking software
About Instasafe Zero Trust
InstaSafe is redefining the challenge of secure access to modern networks by leveraging Zero Trust principles with its security solutions, that ensure seamless access to cloud applications, SAP applications, on-premise data, IoT devices, and multiple other neoteric use cases.
Instasafe discards traditional VPN based conceptions of a network perimeter, instead moving the perimeter to the individual users and the devices they access. The Zero Trust approach followed by InstaSafe mandates a “never trust, always verify' approach to privileged access, without focusing on network locality. InstaSafe ZTAA relies on continuously assessing the trust and risk associated with every user, and the context of their access request, and simultaneously employs a system of comprehensive authentication before grnating least privilege access. By only making authorised applications accessible to the user, and not exposing the network to these users, ZTAA serves to negate the exploitable attacks surface, and also eliminates the threat of insider attacks. In addition, ZTAA ensures that your security teams get complete visibility over all network activity for better identification and remediation of threat vectors.
For more information, visit https://instasafe.com/
Key Products
Zero Trust Application Access | Zero Trust Network Access | Multi Factor Authentication | IAM Identity And Access Management | Secure Enterprise Browser
Key Features
SSO Single Sign On | Endpoint Security | Contextual Based Access Controls | Always On VPN Connection |Clientless VPN | Device Binding | Device Posture Check | Domain Joining
Key Solutions
VPN Alternative Technology | Secure Remote Access Solutions | Cloud Application Security | DevOps Security | VoIP Security Solutions
