How InstaSafe can help Regulated Entities (REs) to stay compliant with SEBI CSCRF guidelines

In a recent circular, dated 20-Aug-2024, Securities and Exchange Board of India (SEBI) has issued a Cybersecurity and Cyber Resilience Framework (CSCRF) for Regulated Entities (REs). From time to time since 2015, SEBI had issued similar advisories to REs with the objective of strengthening cybersecurity measures in the Indian securities market and building adequate cyber resilience against emerging cyber threats.
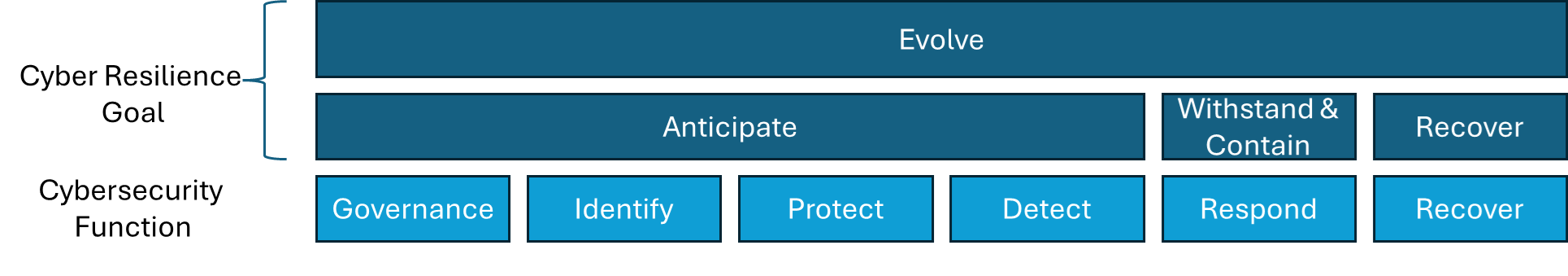
The CSCRF framework covers the five goals of cyber resiliency adopted from Cyber Crisis Management Plan (CCMP) of Indian Computer Emergency Response Team (CERT - In) for countering cyber attacks and cyber terrorism. The Five Goals are - Anticipate, Withstand, Contain, Recover, Evolve. These goals are linked with the following cybersecurity functions - Governance, Identity, Protect, Detect, Respond, Recover.
CSCRF ensures that REs of all sizes should be equipped with adequate cybersecurity measures and cyber resilience capabilities. CSCRF contains provisions regarding procurement of IT services, Software as a Service (SaaS) Solutions, hosted services, audit of software solutions/ applications/ products.
Implementation Period
- For Six categories of REs where cybersecurity and cyber resilience circular already exists - by January 01, 2025
- For other REs where CSCRF is being issues for the first time - by April 01, 2025
CSCRF framework is broadly based on two approaches: cybersecurity and cyber resilience. Cybersecurity approach covers various aspects from governance to operational controls (including Identify, Detect, Protect, Respond, and Recover) and the cyber resilience goals include Anticipate, Withstand, Contain, Recover, and Evolve.
REs are required to comply with the standards and mandatory guidelines as mentioned in the CSCRF.
How can InstaSafe help?
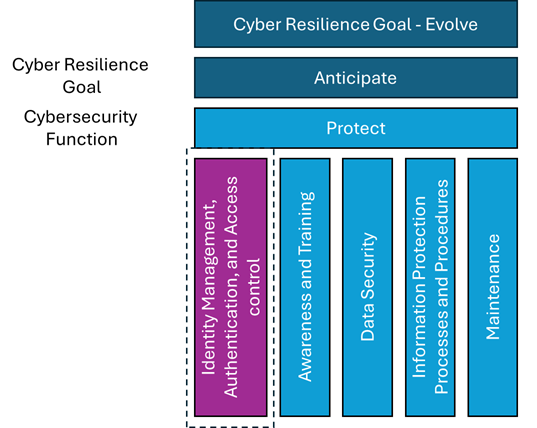
Cyber Resilience Goal: ANTICIPATE | Cybersecurity function: PROTECT
- Guideline on Identity Management, Authentication, and Access Control
1.1 Objective: Access to physical and logical assets and associated facilities is limited to authorized users, processes and devices, and is managed commensurate with the assessed risk of unauthorized access.
1.2 Standard Guidelines
InstaSafe, a proud Make in India brand, helps all regulated entities in providing comprehensive identity management, authentication, and access control solutions with enhanced security controls and better visibility of user and network activity.
Our distributor and partner provide a comprehensive cybersecurity solution to help your organization fully meet CSCRF guidelines. You can email us at sales@instasafe.com or contact us through our website https://instasafe.com/contact-us/
Key Products
Multi Factor Authentication | Identity And Access Management | ZTNA | Zero Trust Application Access | Secure Enterprise Browser
Key Features
Single Sign On | Endpoint Security | Device Binding | Domain Joining | Always On VPN | Contextual Access | Clientless Remote Access | Device Posture Check
Key Solutions
VPN Alternatives | DevOps Security | Cloud Application Security | Secure Remote Access | VoIP Security
