What is the NIST Cybersecurity Framework? All You Need to Know
The growing sophistication of cyber-attacks poses challenges to businesses of all sizes. Hence, understanding cybersecurity risks and managing them with suitable measures is the need of the hour. Organisations today need an effective cybersecurity program to secure their critical resources.
Considering this, the National Institute of Standards and Technology (NIST) at the US Department of Commerce has drafted the Cybersecurity Framework. It aims to address the lack of cybersecurity standards. NIST offers a set of guidelines that organisations in different industries can use. The framework is helping organisations improve their ways of responding and recovering from cyber-attacks by analysing the root causes of such incidents.
Let’s find out more about the NIST framework and how it can provide a robust strategy to tackle cybersecurity challenges.
How Does the NIST Cybersecurity Framework Work?
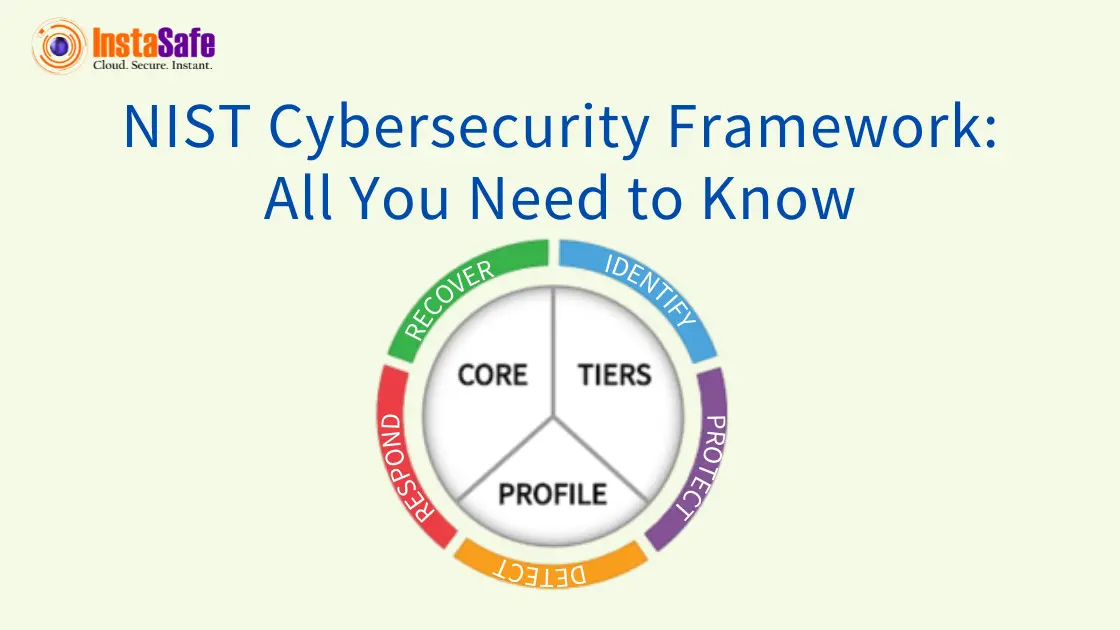
The NIST framework works on the following activities:
- Identification: This step involves identifying the software, equipment and processes that need protection.
- Protection: It involves controlling who logs into the network and uses the company’s assets.
- Detection: It includes a mechanism to detect cybersecurity incidents by monitoring the devices and software for unauthorised access.
- Respond: Responding involves informing the employees, customers and others whose data may be at risk. It helps in containing the impacts of cybersecurity incidents.
- Recover: It involves repairing and restoring the affected equipment and the network.
While every function of the NIST framework is essential, identification is the most crucial aspect. It provides a concrete foundation for your cybersecurity program. Once you identify the assets that require protection, you can apply appropriate strategies to detect the vulnerabilities and protect them. After due detection of the data breach, you can take suitable measures to respond and recover your assets.
NIST Cybersecurity Framework Implementation Tiers
The NIST Cybersecurity Framework has three main components- the Framework Core, Profile and Implementation Tiers. The implementation tiers help evaluate cybersecurity risk management practices a company has incorporated. An organisation can fall into the following four tiers of the NIST Security Framework:
Tier I- Partial
The organisations falling into this tier don’t have cybersecurity practices in place. Due to this, they face challenges while managing cybersecurity risks. Unaware of the cybersecurity threats, these organisations do not exchange cybersecurity information with others endangering the larger business ecosystem.
Tier II- Risk Informed
Organisations in this tier are aware of the cybersecurity threats and deploy risk management practices. But the techniques are informal and not standardised in the entire organisation. They carry out occasional assessments of the cybersecurity structure but do not exchange relevant information with third parties.
Tier III- Repeatable
Tier III organisations have well-laid risk management practices in place. They consistently review and update the policies according to cybersecurity needs and threats. Understanding their greater role in the business landscape, these organisations believe in communicating the associated risks with third parties.
Tier IV- Adaptable
Organisations in this tier are aware of the cybersecurity risks and aim at constant improvement in cybersecurity practices. They adapt themselves to the changing technology and cybersecurity threats and deploy dynamic risk management practices. Understanding the business ecosystem’s risk, Tier IV organisations exchange real-time information with external and internal stakeholders.
Benefits of NIST Cybersecurity Framework
Considering its ample benefits, many businesses and cybersecurity experts are adopting the NIST framework. Here’s how implementing the NIST Cybersecurity Framework can benefit your organisation:
- Provides a Robust Cybersecurity Program
Recognised as the gold standard for cybersecurity, the NIST framework is the collective experience of several cybersecurity professionals. Its implementation allows constant identification and monitoring of possible cyber-attacks and responding to them in real-time. The framework also helps to recover from the cyber threats and analyse the root cause of the incidents.
- Leads to Effective Communication
Miscommunication between an organisation’s leaders and the technical teams is one of the main issues in handling cybersecurity risks. The NIST framework, being the common language of business and technical stakeholders, leads to effective communication in the organisation. This helps contain cybersecurity incidents quickly.
- Flexible and Adaptable
The NIST Cybersecurity Framework is highly flexible and adaptable. You can modify the framework according to your business needs. Also, the NIST Framework is suitable for all types of organisations. It is adopted by several industries varying from critical infrastructure organisations in finance, energy and transport to medium and small industries.
- Enhance Business Growth and Opportunities
Cybersecurity practices hold a key role in business growth and opportunities. By using the industry best practices, you can enhance trust with your business partners. This leads to faster growth of your business along with the security of your critical assets.
Conclusion
NIST Cybersecurity Framework is meant to complement and not replace organisations’ cybersecurity programs. While the NIST framework was designed for Critical Infrastructure, it is highly versatile. With the built-in customisation options, you can customise the framework according to your business needs. NIST Cybersecurity Framework examples include organisations like Microsoft, Intel, Boeing, Nippon Telegraph and many others.
With InstaSafe solutions, you can implement a Zero Trust Security Framework for better user experience, security controls and less complexity. Our Zero Trust Application Access allows you to Secure Single Click Unified Access to SSH/RDR Servers and Applications hosted anywhere.
So, check out the prices today or book a free demo now!
What is Biometrics Authentication | What is Certificate Based Authentication | Device Bind | What is Device Posture | Always on VPN Solutions | What is FIDO Authentication | FIDO2 Authentication | Ldap and Saml | MFA | Password less Authentication | Radius Authentication Server | Security Assertion Markup Language | SAML vs SSO | Software Defined Perimeter | Devops and Security | How to Secure Remote Access | VPN Alternatives | ZTNA vs VPN | Zero Trust | ZTNA | Zero Trust Application Access
