Secure Access for Gitlab

Securely Access Your Gitlab repo with InstaSafe SSO and MFA
Implement additional layer of security with InstaSafe Single Sign On (SSO) and Multi-Factor Authentication to secure your Gitlab code repository
Understanding Gitlab Application
GitLab is an open-source web-based DevOps lifecycle management tool that provides a Git repository manager for managing source code repositories, version control, and DevOps lifecycle with features like issue tracking, CI/CD (Continuous Integration/Continuous Deployment), and more.
Current Challenges with Secure Access for Gitlab Application
- Risk of unauthorized access by outsider- Gitlab repositories often contain proprietary source code and other confidential information such as user credentials, API keys and other configuration files. Provisioning direct access to Gitlab repository over internet can have pertinent risks of unauthorized access.
- Risk of unauthorized access by insider - In case a employee leaves the organization, often the IT admin forgets / take few additional days to remove the access. The departing employee can have access to gitlab repository posing significant risks
- Lack of strong authentication mechanism - Current authentication methods involve password as primary authentication and OTP as secondary authentication (which is optional).
With InstaSafe Secure Access for Gitlab, You can
- Hide your applications from public internet with self managed Gitlab deployment
Self managed Gitlab instance will only be accessed through InstaSafe agent after the user is authenticated and provisioned. Gitlab instance will not be available to access through direct URL thereby eliminating any risks of data breach.
- Seamless and one-click access of Gitlab applications using Single Sign-On (SSO)
With Single Sign-On, gets authenticated once and seamless access application. No need to sign in frequently and remember different credentials for different applications.
- Multi-factor authentication (MFA) for additional security
Use additional authentication methods such as OTP, T-OTP, push notifications, Biometrics notifications, Hardware token to eliminate the risks arising from password breaches
- Enforce device authentication to ensure only authorized device gets access
Ensure only authorized and compliant devices provided by organization is able to access to application after proper authentication. Device identity is key to significantly reducing the chances of data breaches and ensuring right user with right device is accessing application
Once InstaSafe SSO is configured, here is the scenario for accessing self managed Gitlab without / with InstaSafe
Step by Step Guide for configuring SAML Single Sign On for Self Managed Gitlab
Cloud provider for hosting Gitlab
Various cloud providers, including AWS, Google Cloud Platform, Microsoft Azure, DigitalOcean, and others, offer robust infrastructure options for deploying self-hosted GitLab instances. Each provider supports scalable virtual machines, managed databases, and Kubernetes services, providing flexibility and customization for organizations seeking control over their DevOps environments.
AWS
To set up GitLab on AWS following your specifications, here's a step-by-step explanation:
Instance Selection: Choose an appropriate instance type depending on your usage requirements, such as r6i.large. This instance type provides sufficient resources for GitLab's operations.
VPC and Subnet Configuration:
- Ensure you have a Virtual Private Cloud (VPC) set up in AWS.
- Choose an availability zone within your preferred region for high availability.
- Select a subnet within the chosen VPC and availability zone where the GitLab instance will reside.
Elastic IP Configuration:
- Allocate an Elastic IP (EIP) address to your instance to ensure a static public IP that persists even if the instance is stopped and restarted.
Security Group Configuration:
- Create or modify a security group to allow inbound traffic on ports 443 for GitLab access via InstaSafe ZTAA.
- Configure outbound rules to allow all traffic from the instance to communicate with external services and repositories.
Instance Launch and Setup:
- Launch the instance with the chosen specifications (instance type, subnet, security group).
- Connect to the instance using SSH or AWS Systems Manager Session Manager.
GitLab Installation and Configuration:
- Update the instance and install the necessary packages (e.g., Docker, GitLab dependencies).
- Follow GitLab's official installation guide or use Docker to deploy GitLab.
- Configure GitLab settings, including domain name configuration, SSL certificates (using Let's Encrypt or your own certificates for HTTPS access), and GitLab administrative settings.
- Set up repositories, users, and permissions as per your organization's requirements.
Once GitLab is successfully hosted on AWS or any other cloud provider, the administrator can proceed to configure access via the InstaSafe portal with the following steps:
- In the perimeter management navigate to applications and create a gitlab application and give the self hosted gitlab url.
- Save the configuration settings for the GitLab application.
- Navigate to the "Access Policy".
- Create a new policy specifically for GitLab access.
- Add the relevant users or user groups who require access to GitLab.
- Include the GitLab application within the application configuration.
- Update and save the policy settings to apply the access controls.
- Add the application behind the gateway in InstaSafe portal.
- Once the setup in the portal is done.
- The user can go to the self hosted Gitlab page and can login to Gitlab using the InstaSafe Single Sign On.
- The user can connect to the InstaSafe ZTAA agent and access the gitlab.
When the agent is disconnected, the user will not be able to access the gitlab.
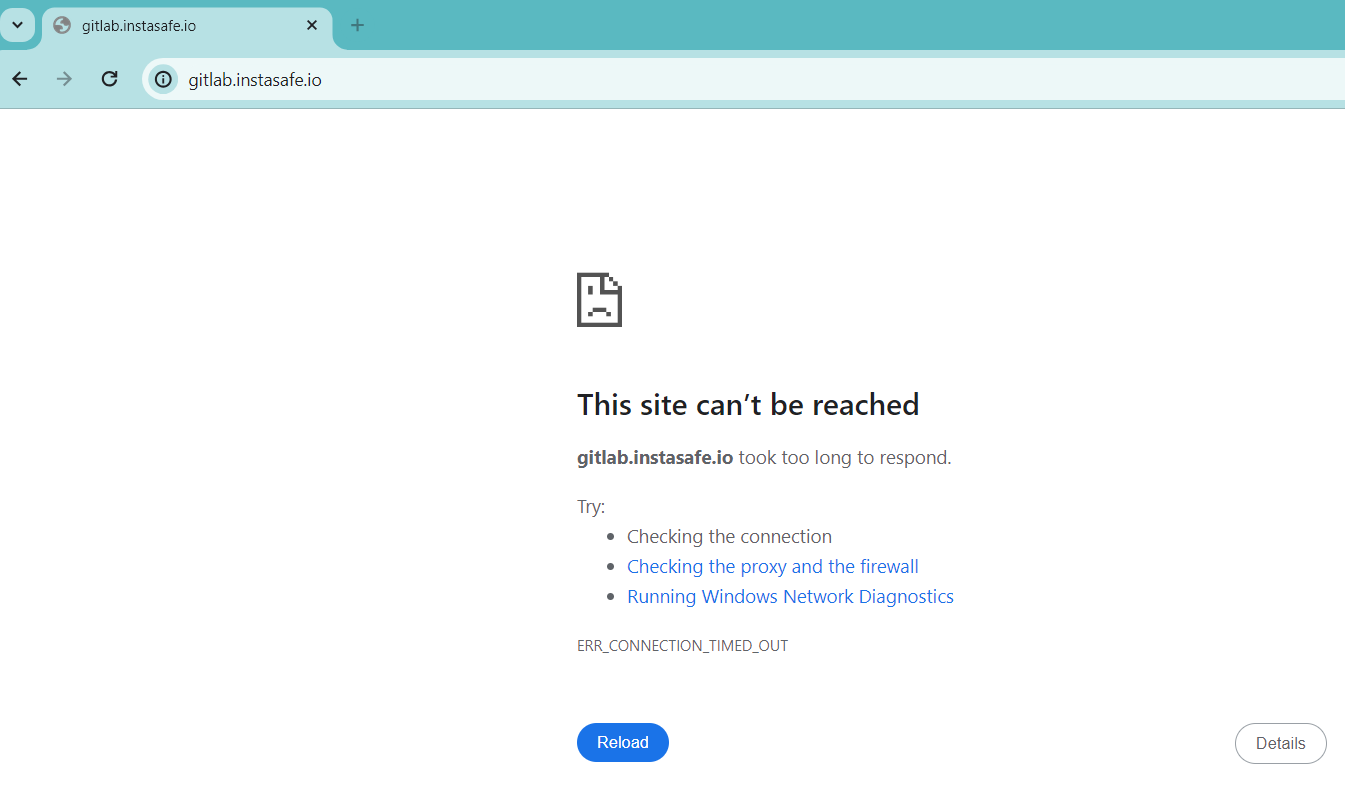
Above image shows that after SSO configuration, directly accessing self managed Gitlab instance is not possible directly from the browser. Only using InstaSafe agent and accessing through InstaSafe secure browser, Gitlab instance is accessible
Benefits of InstaSafe Secure Access for Gitlab
- Granular Access controls - Provision user or user groups based on their role on who can access
- Complete visibility - Get complete visibility of user activity for better insights
- Better Security - MFA and SSO provides enhanced security with seamless user experience
- Easy to Deploy - Secure Access can be set up in minutes and easy to get started.
Complement our other Solution Stack
Single Sign On: Validation and Authentication from a single dashboard, using a single set of credentials, gives you access to all authorized applications, whether on-premise or on the cloud
Multi Factor Authentication: Add additional layer of authentication with OTP, T-OTP, PIN, Biometrics or push notification.
Contextual Access: Leverage IP based Access, Time based Access, Geolocation based access and Device based access for added flexibility and agility
Secure Identity Cloud: Comprehensive identity and access management solution to manage and control access to digital resources
To book a demo, please visit https://instasafe.com/book-a-demo
