Privileged Access Management
InstaSafe Privileged Access Management (PAM) is the key to safeguarding sensitive information, preventing unauthorized access, and maintaining the integrity of critical systems. This article delves into the fundamentals of PAM, its workings, types of privileged accounts, features of PAM solutions, and best practices for successful implementation.
What is Privileged Access Management (PAM)?
Privileged Access Management (PAM) is a cybersecurity strategy and set of technologies designed to secure, manage, and monitor privileged access within an organization's IT environment. Privileged accounts, which possess elevated permissions, are systematically controlled to mitigate the risk of misuse and protect against potential security threats.
How Does PAM Work?
PAM works by implementing a range of security controls to manage and monitor access to privileged accounts. The core functionalities include:
- Privileged Account Discovery:
- Identifying all privileged accounts within the network.
- Maintaining an inventory for comprehensive visibility.
- Credential Vault:
- Safely storing and encrypting privileged account credentials.
- Automating password changes to reduce the risk of unauthorized access.
- Access Control: (Refer Documentation here)
- Enforcing the principle of least privilege.
- Implementing role-based access controls for streamlined management.
- Session Monitoring and Recording:
- Real-time monitoring of privileged user sessions.
- Capturing and storing session activities for auditing purposes.
- Multi-Factor Authentication (MFA): (Refer Documentation here)
- Adding an extra layer of authentication for privileged accounts.
- Adapting authentication requirements based on contextual factors.
- InstaSafe PAM provides native integration with multiple MFA solutions including: SMS OTP & Email OTP, Biometric devices, App based OTP, Soft Tokens, Hard Tokens, PKI Signature Tokens, Mobile Token, Email Token, and SMS Token.
- Each token generated from the solution is unique to each user. It has six - digit numerical passwords. Token regeneration takes place quickly and is sent to Email/sms gateway. Token is time synced with authentication server. All Tokens are AES encrypted.
- Biometric Authentication includes fingerprint authentication for all ten fingers and continuous facial authentication.
- Single Sign-On (SSO): (Refer Documentation here)
- SSO to all types of applications including Windows servers, Unix/Linux, Web Applications and gives access to users without disclosing the passwords.
- Single Sign on to all types of target devices including Servers, Databases, Routers, Switches, Firewalls, Applications, Thin Clients, Thick Clients, Client Server Applications, Application GUIs etc.
Types of Privileged Accounts
There are various types of privileged accounts, including:
- Administrator Accounts:
- Possessing broad access across systems and networks.
- Often used for system configuration and maintenance.
- Root Accounts:
- Highest level of access on Unix/Linux systems.
- Can make changes to system files and configurations.
- Service Accounts:
- Used by applications and services to perform specific functions.
- Often granted elevated privileges for seamless operation.
Features of InstaSafe PAM Solution
- Just-In-Time Privilege Elevation:
- Granting elevated access only when needed and for a specified duration.
- Session Isolation:
- Ensuring privileged sessions are isolated from non-privileged users.
- Audit and Compliance Reporting: (Refer documentation here)
- Generating comprehensive logs of privileged activities.
- Facilitating compliance with regulatory requirements.
- Integration with IT Infrastructure:
- Integrating with directory services for authentication and authorization.
- Collaborating with other security solutions for enhanced protection.
- Integration with SIEM and GRC tools with REST API.
- Integration with MFA and Radius Server.
- Supports Single Sign-On using SAML, OAuth and OpenID.
- Remote Access:
- Access using a secure browser in a container environment.
- supports both agent and agentless access.
- Access to Web Apps, Thick client, Windows and Linux servers.
- Limit access to users to access certain applications using RDP/ SSH sessions.
- InstaSafe PAM integrates with all types of applications including web applications, thick clients and also native applications of customer out of box without any adaptor or connector.
- Automated Patch Deployment:
- Automated deploy patches missing in the network computer without manual intervention
- Alerts and Notifications
- Alerts to administrator in case of any bypass or direct access.
- Browser Agnostics:
- InstaSafe PAM is browser neutral and can be accessed from Chrome, Firefox or IE Browsers without any dependency on agents or plugins.
Best Practices for PAM Implementation
- Comprehensive Assessment:
- Conducting a thorough evaluation of privileged accounts and associated risks.
- Role-Based Access Control (RBAC):
- Implementing RBAC to assign permissions based on job roles.
- Regular Training and Awareness:
- Educating users about the importance of privileged access security.
- Continuous Monitoring:
- Implementing real-time monitoring and anomaly detection.
- Regular Audits:
- Conducting regular audits to ensure compliance and identify vulnerabilities.
- Incident Response Planning:
- Developing a robust incident response plan for quick and effective action.
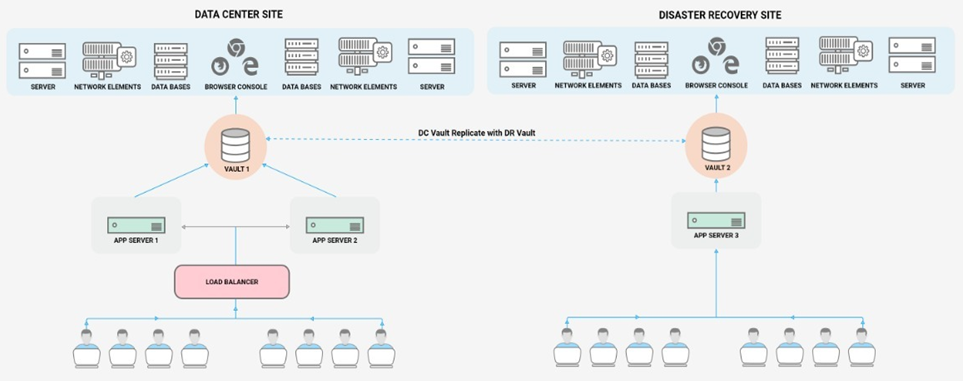
Deployment Model
InstaSafe PAM can be deployed in hybrid environment (both cloud and on-premise). InstaSafe PAM deployment supports high availability using Active-Active or Active-Passive approach. Multiple Appliances/Virtual Machines can be deployed in DC and DR to ensure high redundancy in the system. InstaSafe PAM portal is accessble over web using any web browser. There is no limitation for accessibility.
This solution is highly scalable – horizontally [adding more application nodes] as well as vertically [increasing the VM sizing] and can manage thousands of privileged user session and hundred thousand plus devices. InstaSafe PAM solution is extensible and scalable to ensure it is capable of meeting complex operational requirements of customers as well as compliance requirements issued by regulators or standards organizations worldwide.
Incorporating Privileged Access Management (PAM) into your cybersecurity framework is critical for fortifying your defenses against unauthorized access and potential security threats. By understanding the workings of PAM, recognizing the types of privileged accounts, leveraging key features of PAM solutions, and following best practices for implementation, organizations can establish a resilient security posture that safeguards their most sensitive assets.
Refer Documentation: https://docs.instasafe.com/ZeroTrustEnterprise/003-gettingstarted/
