Privilege Session Manager

In the intricate landscape of Privileged Access Management (PAM), one of the keystones for securing sensitive information is the Privilege Session Manager. This specialized solution plays a vital role in orchestrating security measures, enabling organizations to monitor, control, and audit privileged user sessions. This article delves into the significance of Privilege Session Managers within the broader framework of PAM, exploring their key functionalities and the substantial benefits they bring to the realm of cybersecurity.
Unveiling Privilege Session Manager:
Privilege Session Manager is a sophisticated tool designed to oversee and manage privileged user sessions within an organization's IT environment. By providing granular control over privileged access, it adds a layer of security that is indispensable in safeguarding critical systems and sensitive data.
Key Functionalities of Privilege Session Managers:
- Real-Time Session Monitoring:
- Actively monitoring privileged user sessions in real-time.
- Detecting and responding to any unusual activities or potential security threats.
- Browser agnostic- works on any browser.
- Session Recording:
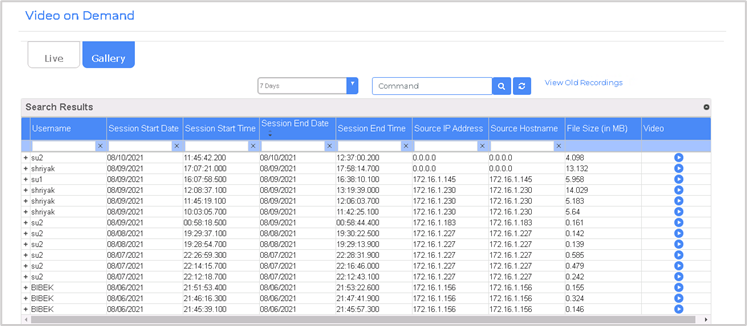
- Capturing detailed logs of privileged user sessions.
- Creating an audit trail for forensic analysis and compliance purposes.
- Real time session recording of privilege users.
- Real time viewing and session recording of any session initiated via PAM including servers, network devices, databases, applications or thick clients etc
- Session Isolation:
- Ensuring that privileged sessions are isolated from non-privileged users.
- Preventing unauthorized access and potential lateral movement.
- Just-In-Time Privilege Elevation:
- Granting elevated access only when necessary and for a specified duration.
- Minimizing the window of opportunity for potential security threats.
- Access Control Policies:
- Defining and enforcing access control policies based on roles and responsibilities.
- Restricting access to sensitive resources during privileged sessions. That includes password from PAM vault.
- Comprehensive Audit Trails:
- Providing detailed records of all actions taken during privileged sessions.
- Facilitating compliance audits and regulatory requirements.
Advantages of Privilege Session Managers in PAM:
- Proactive Security Measures:
- Identifying and responding to security incidents in real-time.
- Enabling organizations to take proactive measures to mitigate potential threats.
- Forensic Analysis and Compliance:
- Creating detailed logs for forensic analysis in the event of a security incident.
- Assisting organizations in meeting compliance requirements through comprehensive audit trails.
- Reduced Attack Surface:
- Minimizing the attack surface by isolating privileged sessions.
- Limiting the impact of potential security breaches.
- Efficient Resource Utilization:
- Optimizing the use of privileged resources by granting access only when required.
- Streamlining session management for improved operational efficiency.
- Enhanced Accountability:
- Establishing user accountability through detailed audit trails.
- Encouraging responsible and secure practices among privileged users.
Implementing Privilege Session Managers - Best Practices:
- Comprehensive Assessment:
- Conducting a thorough evaluation of privileged access requirements.
- Identifying critical sessions and resources that require heightened security.
- Continuous Monitoring:
- Implementing continuous monitoring to detect and respond to real-time threats.
- Ensuring that privileged sessions are actively supervised.
- Policy Enforcement:
- Enforcing access control policies to restrict and manage privileged sessions.
- Defining and implementing policies aligned with organizational security goals.
Conclusion:
Privilege Session Managers emerge as indispensable assets in the arsenal of Privileged Access Management solutions. By orchestrating security measures, these tools empower organizations to maintain control over privileged user sessions, proactively respond to potential threats, and adhere to stringent compliance requirements. Embracing Privilege Session Managers is a strategic step towards fortifying the security posture of organizations in an ever-evolving digital landscape.
Refer Documentation:
